| Sections Below | |
| Choosing a Subnet | Subnet Masks |
| Static IP Addresses | Putting It All Together |
| Gotcha | VLANs |
| Router Attacks Based on IP address | |
Introduction
As you would expect, every computing device on a network has a unique number. And, by "computing device," I mean any desktop computer, phone, tablet, ROKU box, router, printer, smart TV, Amazon Echo etc. etc. etc. The unique numbers are called IP addresses and they are written as four decimal numbers separated by periods (rather than commas). A common IP address is 192.168.1.1. The IP address for this website is 216.92.136.14.
For the networking experts reading this, I am ignoring IPv6 because the purpose here is a simple explanation for non-techies. Also, it is never used on a LAN.
Each number can range from zero to 255. This is because, under the covers, an IP address is really a 32 bit binary number. Nobody wants to deal with binary numbers directly, so we use a decimal number to represent 8 binary digits (better known as bits). Two to the 8th power is 256 and that is why the numbers in an IP address range from 0 to 255.
Routers differ from other computing devices in that they have (at least) two IP address: a public one and a private one.
The public side of a router is visible on the Internet. The public side is also referred to as the WAN or Wide Area Network side of the router. The router has no control over the public IP address, it is assigned by the ISP (Comcast, Verizon, Spectrum, etc.). The public IP address is not a secret and there are many websites that display it (ipchicken.com, checkip.dyndns.com and www.ip-adress.com/what-is-my-ip-address). The IP address for this website (see above) is a public IP address. All the devices in your home/office share the same public IP address.
Some high end routers can handle two concurrent connections to the Internet. In that case, all the devices connected to the router share two public IP addresses.
In contrast, the router has total control over the private side (a.k.a. LAN or Local Area Network side) IP addresses, both for itself and for all the computing devices that connect to it.
The range of allowable LAN side IP addresses is called a subnet (as in sub-network, as in, only use these few numbers of all the billions of possible numbers). A very common subnet (range of numbers) is the numbers that start with 192.168.1 and vary in the fourth/last number. This is often written as 192.168.1.x where the x is a placeholder for all the possible numbers in the fourth position (0 to 255).
Devices that connect to the router get assigned a LAN side IP address in one of three ways.
- The most common is that they ask the router to give them an IP address when they first connect to the network. This is referred to as DHCP, where the D stands for dynamic, as in the IP address is dynamically assigned when requested. A device typically uses an IP address for a day and then asks the router for another one, but the router can control this.
- A slight variation on this also uses DHCP, but the router will always give the same device the same IP address, over and over and over and over. A common term for this is DHCP reservation.
- The least popular method is for a device to be configured to use the same IP address all the time. That is, it never asks the router for an IP address. The opposite of Dynamic, this is referred to as a static IP address. If the static/fixed IP address is not in the correct sub-network, hair will be pulled out.
These are the decisions that need to be made regarding LAN side IP addresses:
- Pick a subnet (the full range of allowable IP addresses). This, in turn, requires the specification of a Subnet Mask (more below)
- Assign a fixed IP address within the subnet to the router
- Decide which IP addresses within the subnet will be given out on a dynamic (on-demand) basis to devices that connect to the router.
Every router has default values for the three decisions above and the defaults will, of course, work. Dealing with IP addresses and subnets is optional when configuring a router, but recommended for a few reasons.
For one, you will be a bit safer by not using the defaults. This is because some malware targets routers by their default IP address. Also, some devices on the Local Area Network work best with a static/permanent IP address and the defaults for your router may not allow for any static IP addresses. Using a subnet that is off the beaten path can also come in handy for VPNs. If, someday in the future, you setup a site to site VPN, having each site use its own subnet is cleaner and easier. And, should you ever want, or need, to plug one router into another router, it will not work well if each router uses the same subnet.
FYI: There are two reasons to plug one router into another. The first is to make some initial configuration changes to a new router, as I suggest on the new router page. The other is carve out a secluded section within your home for devices involved in working from home. For more on this, see my September 2020 blog A second router can make working from home much more secure.
The downside to configuring IP addresses and subnets is that a mistake can totally screw things up. So, the three decisions mentioned above (and detailed below) are best done early in the router configuration game. This way, if the change screws things up, the router can be reset without losing any other configuration changes you may have made.
Choosing a Subnet top
The first decision is the subnet, which specifies the range of allowable IP addresses on the LAN. This range also determines the maximum number of devices that can connect to the router. For most people, most of the time, a range that allows for 250 connected devices (give or take) should be sufficient. Pretty much every home router uses a subnet that supports a maximum of 250 connected devices.
A subnet that allows for 250 devices is specified with the first three numbers of the four numbers in an IP Address with an X serving as a wildcard. For example, very popular subnets are 192.168.0.x, 192.168.1.x and 192.168.2.x. Because they are popular, they are best avoided. Using a subnet such as 192.168.200.x makes you a bit safer because no router uses subnet 192.168.200.x by default.
A subnet of 192.168.200.x means that all devices on the network will have IP addresses that start with 192.168.200. It also means that the network can not contain more than 256 devices (recall that each portion of the IP address ranges from zero to 255). But, the highest and lowest IP addresses often have special meanings, so I would limit this subnet to 192.168.200.1 (avoiding zero) through 192.168.200.253 (skipping 254 and 255). Thus, a max of 253 concurrently connected devices.
Why the devotion to subnets that start with 192.168?
Some IP addresses are not allowed on the public Internet, they are reserved for internal (LAN side) use only. That is, you can, and should, use them in your home or office. IP addresses that start with 192.168 are on this reserved list. So too are all the IP addresses that start with 10. You will never find any IP address on the public Internet that starts with either a 10 or with 192.168. Meanwhile, every home in the world can use the 192.168.1.x subnet without a problem.
Whether you opt for a subnet that starts with 192.168 or one that starts with 10, it is best to avoid subnets used by other devices.
If you prefer 192.168, then avoid networks where the third number is:
- 0, 1, 2, 3 (used by Amped Wireless, Huawei and many others)
- 4 (used by Zoom and eero)
- 5 (used by Hawking)
- 7 (used by Eero)
- 8 (used by GL.iNet and Huawei)
- 9 (used by Gryphon)
- 10 (used by Motorola,MSI,pcWRT,TRENDnet,NetComm)
- 11 (used by Buffalo)
- 15 (used by D-Link, Linksys and Vonage)
- 16 (used by Linksys)
- 19 (used by Anonabox)
- 20 (used by Motorola,NetComm)
- 30 (used by Motorola)
- 50 (used by Peplink)
- 55 (used by Luma)
- 62 (used by Motorola)
- 72 (used by Asus Lyra)
- 85 and 86 (used by Google)
- 88 (used by MikroTik)
- 100 (used by assorted cable modems and Huawei)
- 102 (used by Motorola)
- 121 (used by the Ubiquiti Alien router)
- 123 (used by LevelOne, Sitecom, Comfast)
- 127 (used by Mercku)
- 168 (used by Sonicwall)
- 178 (used by AVM FRITZ!Box)
- 179 (used by AVM FRITZ!Box Guest network)
- 218 (used by Firewalla)
- 223 (used by Trendnet)
- 254 (used by D-Link, Actiontec)
In September 2018, malware was found looking for routers on the 192.168 dot 0, 1, 2, 15, 25 and 100 subnets, an extra good reason to avoid them.
If you prefer IP addresses starting with 10, then the subnets to avoid are
- 10.0.0.x (Netgear, Asus, Cisco, Rogers Ignite, 2Wire, etc)
- 10.0.1.x (Apple)
- 10.1.1.x (Belkin, D-Link)
- 10.1.10.x (SMC)
- 10.10.1.x (Asus)
- 10.10.10.x (HooToo in their HT-TM05 TripMate Titan Wi-Fi sharing device)
- 10.90.90.x (D-Link)
Some easy to remember networks would be 10.11.12.x and 10.20.30.x. That said, easy to remember should not be a priority, security should be. So, something that no one would guess, like 10.43.27.x is better. If you live at 123 Main Street, then 10.123.123.x is a great choice.
If you know of other default subnets used by routers, please send me an email.
To really live off the beaten path, you can chose a subnet between 172.16.x.x and 172.31.x.x. These too, are reserved for LAN-side use only and, I suspect, used much less often than 10.something and 192.168.something. For example, I have never seen or heard of a router that uses one of these subnets by default. My guess is that they are un-popular because they are harder to remember. Then too, their subnet masks (next topic) are non-standard and there may be some routers that do not support it.
Finally, there is yet a third category of IP address, one that is neither reserved for home use nor available on the public Internet. Way back when, Internet Service Providers had more customers than they had public IP addresses. They could have assigned their customers IP addresses that start with 10 and put them behind a big router. Conceptually, this NAT setup would be the same as we have in our homes. Perhaps some did it this way. But, years back, a new clump of IP addresses was reserved for ISPs. This clump is called Carrier Grade NAT or CG-NAT or a bunch of other names. The IP addresses range from 100.64.0.1 to 100.127.255.254. This is expressed in techie terms as 100.64.0.0/10 (see the Subnet topic below).
If your Internet connection uses CG-NAT then the public IP address that your router sees will be in this 100.x.x.x range while a query for your public IP address will return a different IP address. Tailscale also uses this range of IP addresses as they explain here: What are these 100.x.y.z addresses?.
Subnet Masks top
Hand in hand with picking a subnet, is the concept of a subnet mask. The mask is half of what defines your subnet. The bad news is that subnet masks are bit (binary digit) masks and thus confusing for non-techies. The good news is that almost every home network uses the same subnet mask, so chances are that you can skip the details.
The subnet mask for any network where the first three numbers are the same is 255.255.255.0. The 255 means that that part of the IP address is part of the subnet, the 0 means that it is not. So, 255.255.255.0 means that the first three numbers are being used to define the subnet. Thus, 192.168.1.x and 192.168.22.x and 10.11.11.x and 10.88.99.x can all use a subnet mask of 255.255.255.0 because, in each case, the first three numbers are the same and define the subnet.
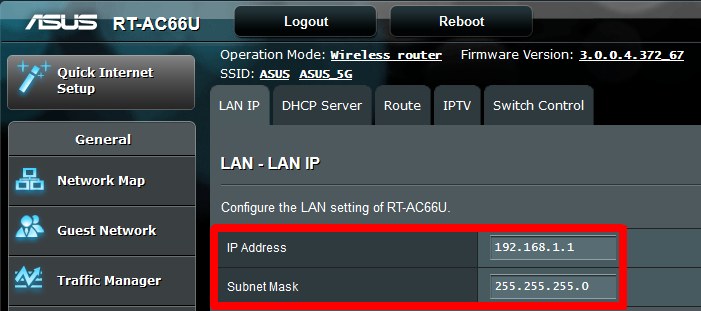
The image above shows how you define the subnet for an Asus router. The subnet mask goes hand in hand with assigning the router an IP address (our next topic below). All devices connected to the router will have an IP address that starts with 192.168.1.
Most people can stop reading this section here. Chances are your router will pick a subnet mask of 255.255.255.0 by default. A bad router might not let you use anything else.
A subnet mask of 255.255.255.0 is actually 24 binary ones, followed by 8 binary zeros. For this reason, you often see it referred to as 255.255.255.0/24.
Shorthand lingo: for techies writing 11111111111111111111111100000000 is out of question. But even writing 255.255.255.0 is too much, so the slang term for this subnet mask is a "slash 24" where the 24 means the first 24 bits are ones. And, again, only the ones matter, the zeros do not. A subnet mask of 255.255.0.0 would be called a "slash 16". This will not be on the test :-)
The only time you are likely to run into a subnet mask other than 255.255.255.0 is creating an outbound firewall rule (there is more on this on the page for configuring a Surf SOHO router. For example, to block transmission to any IP address that starts with 123.123, you would use a subnet mask of 255.255.0.0 in the firewall rule (a.k.a. a slash 16). To block transmission to any IP address that starts with 123, you would use a subnet mask of 255.0.0.0 (a.k.a. a slash 8). On the other end of the scale, to block access to this website (its public IP address is 216.92.136.14) you would use a subnet mask of 255.255.255.255 (a.k.a. a slash 32).
THE HARD PART
Any IP address that starts with 192.168 is reserved for internal/LAN use only. Thus, you could have 192.168.5.5 and 192.168.6.6 and 192.168.33.22 all be part of your home subnet. If you do, then your router could, in theory, communicate with over 65,000 devices. In reality, you would not want to pay for a router with the computing horsepower to handle 65,000 devices. Still, for the rich people out there, you would indicate this with a subnet mask of 255.255.0.0 or 255.255.0.0/16.
IP addresses that start with 10 are even more flexible. On the low end, they can mimic the 192.168.1.x subnet and have the first three numbers all be the same, which allows for 253 devices. In the examples above, I assumed this would be the case. As before, the subnet mask would be 255.255.255.0.
On the high end, they can simply have just the 10 be same and let all the other numbers vary. In this case, 10.1.2.3, 10.4.5.6 and 10.123.123.123 are all part of the same subnet. This allows for over 16 million devices on the subnet. Don't do this. You don't need 16 million devices connected to your router. That said, this would be indicated by a subnet mask of 255.0.0.0 or 255.0.0.0/8.
On the high end, subnets between 172.16.x.x and 172.31.x.x can use a subnet mask of 255.240.0.0/12 and have over a million devices on the subnet. They should also work fine with the most common subnet mask (255.255.255.0) indicating a subnet where the first three digits are all the same and supporting up to 253 devices. A subnet mask of 255.240.0.0 is really off the beaten path and there is a chance that a router may not even support it.
Whew.
Static IP Addresses (such as the router) top
Within a given subnet, there is, at the least, a single static (aka fixed or never-changing) IP address, that of the router. Typically, the router is assigned the number 1. For example, on the 192.168.1.x subnet, the router will almost always be assigned IP address 192.168.1.1. Likewise, on the 10.11.12.x subnet, the router is likely to be given IP address 10.11.12.1. There is no technical requirement for this, it's just a custom.
This custom, however, makes it easier for malware to find the router, so you are a bit safer if your router is not device number 1. In fact, I would avoid assigning anything to the number 1.
For example, in September 2018, malware was found targeting routers on 7 different subnets, but in each case it assumed the router's IP address ended in 1.
The second most popular IP address for a router is one that ends with 254, as shown in this Dec. 2017 article: A List of Common Default Router IP Addresses. So, 254 is out too.
Zero often has a special meaning when it comes to computer networks, so it is best not to use zero either. That leaves 2 through 253 on a typical subnet (one with a maximum of 256 devices).
But, Trend Micro says not to use IP addresses ending in 100 for the router. See Protecting Home Networks: Start by Securing the Router May 18, 2017.
So, what to do?
You get the most flexibility by using either a low (2,3,4, 5) or high (250, 251,252,253) number. Again, the LAN side IP address of the router is always static, it is the public IP address of the router that typically changes over time.
So, what about the rest of the subnet? If the router is given number 4, what should we do with numbers 5 through 253? They could all be used for dynamic addresses via DHCP and that works fine. In fact, it is the default with consumer routers. But, if you are up to it, it is best to set aside a few numbers for static IP addresses. I say this because some devices function much better with a fixed IP address. The two most obvious examples are a shared network printer and a NAS (Network Attached Storage) device. This is not a security thing, it's a make-my-future-life-easier thing.
So, for example, if the router is device number 4, maybe start the DHCP range of IP addresses at 10 or 15, rather than 5. On the other end, maybe end the DHCP range at 250 rather than 253.
February 2024: Finally, a web browser is adding some protection for the devices in your Local Area Network. From: New Google Chrome feature blocks attacks against home networks by Mayank Parmar for Bleeping Computer (February 17, 2024). Chrome will now be on the lookout for public websites that try to access a device in your home. Quoting: "Google is testing a new feature to prevent malicious public websites from pivoting through a user's browser to attack devices and services on internal, private networks. More simply, Google plans to prevent bad websites on the internet from attacking a visitor's devices (like printers or routers) in your home... " The feature will be called "Private Network Access protections" and it will be released in Chrome version 123. Initially, Chrome will just warn about this, eventually, it will block by default (I assume). This feature should have existed decades ago. Hopefully other browsers will follow suit.
Putting It All Together top
To sum up: We first need to pick a subnet that is off the beaten path, then pick an IP address within that subnet for the router (also, one off the beaten path). Then, finally, pick a range of IP address to be used by DHCP, with the remaining ones available for static assignments.
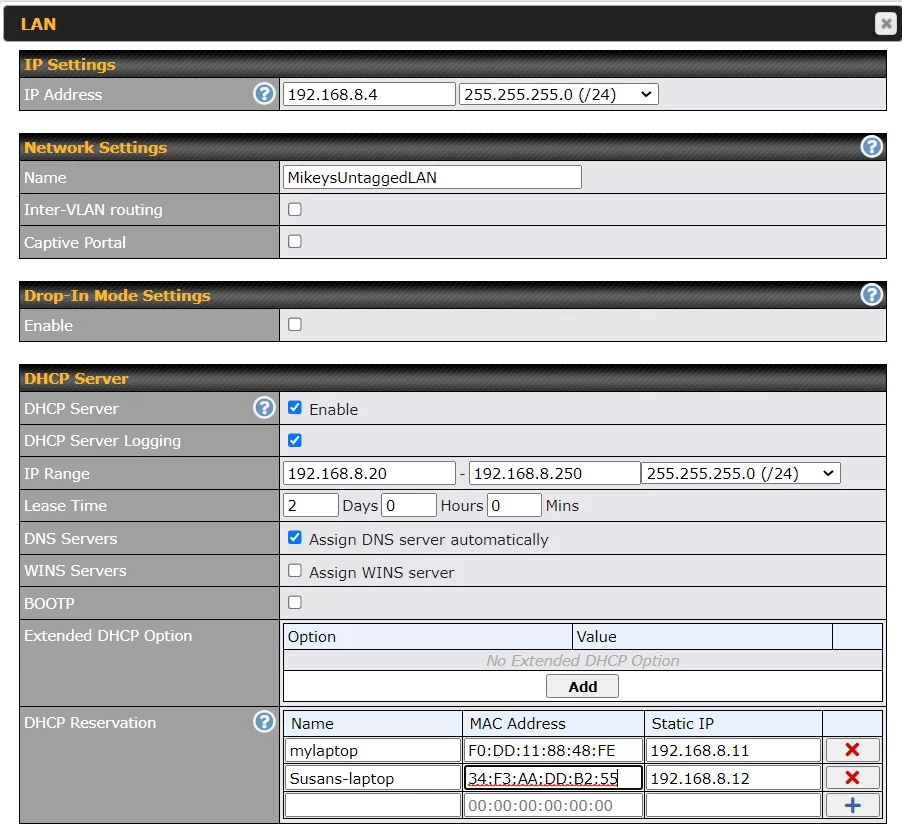
The image above shows how to define a subnet for a Peplink router. Peplink makes high end hardware so there are far more options here than are available on a consumer router.
The IP Address field at the top is poorly labeled, it is the IP address of the router on the LAN subnet. The router is device number 4 on the 192.168.8.x subnet. Next to this is the subnet mask. We can ignore the next two sections (Network Settings and Drop-In Mode Settings).
The IP Range field is also poorly labeled, it is the DHCP range, the range of IP addresses that the router will give out dynamically. In this case, the router is using IP addresses from 20 to 250 for DHCP. This means 1-19, excluding 4 (for the router), can be used for static/fixed/permanent IP address assignments. That said, I would avoid 1. It also means that 251, 252 and 253 are also available for static IP addresses. Note again, that the router's own IP address has to be outside of the DHCP range. My experience has been that some routers are smart enough to automatically adjust the DHCP range on their own, when the IP address of the router is changed. Still, can't count on that. For whatever reason, Peplink requires you to specify the subnet mask here too.
Dynamic IP address assignments expire. If they did not, networks would, sooner or later, run out of available IP addresses. The "Lease Time" is how long a device can use its router-assigned dynamic IP address. After the lease has run out, a device has to ask the router again for an IP address. Will it get the same one? Probably, but there is no guarantee. Note that Asus routers make you specify the lease time in seconds. Peplink is better, as it deals with days, hours and minutes.
Finally, take note of the "DHCP Reservation" section at the bottom. This is optional and not related to security.
There are two ways that a device can have a fixed/static IP address. The first way is harder, it requires configuring the device with the static IP address and making sure that said address is outside of the DHCP range. Have you ever tried to configure a network printer using the small screen on the printer? Ugh. The second approach is easier and Peplink calls this DHCP Reservation.
The second method lets devices use the default/normal method of getting a LAN-side IP address: DHCP. The problem with DHCP is that after the lease on an IP address expires, a device may be assigned a different one. Most of the time, this matters not at all. But when it does matter (think NAS or printer), DHCP Reservation insures that the same device always gets the same IP address. It is a hybrid approach. The IP address may be in the DHCP pool, but, nonetheless, it will always be assigned to one and only one device.
In the example above, the two devices are assigned IP addresses 11 and 12 which are outside the DHCP range. This is not required, it's just logically neater.
The DHCP reservation is made by assigning a MAC address to an IP address. Such a simple statement, but one that opens up a can of worms.
What's a MAC address? Long story.
In the old days it was a unique identifier for a computing device. You could think of it as a serial number for the hardware component that connected a device to a network. That said, even in the old days a laptop had one MAC address for Wi-Fi and a different one for Ethernet. Now, things are more complicated. Your personal privacy has been enhanced in a number of operating systems by not always using the same MAC address. The idea was that you could, in theory, be tracked via the MAC address of your device. That said, only the router sees the MAC address, it was never available on the Internet.
Windows 10 calls the not-re-using-a-MAC feature Random Hardware Address. Apple iOS calls it a Private Wi-Fi address. Now it is normal for your device to present a different Wi-Fi MAC address for each different Wi-Fi network that it connects to.
Gotcha top
Using a non-standard subnet and assigning the router a non-standard IP address makes your network safer, but it is not a perfect defense.
For one thing, a service called WebRTC, that runs inside a browser, can leak the internal IP address of the router. The Test your Router page has links to a number of online tester pages that report whether WebRTC is enabled in your web browser. If you don't use WebRTC, then you will be safer having it disabled in every web browser that you use. Many of the tester pages have instructions for disabling it. The Ublock Origin browser extension can disable WebRTC, but does not disable it by default.
Another way the internal router IP address can leak is via the hard coded domain names used by some routers. To make it easier to access the web interface of a router, Netgear lets its customers use www.routerlogin.com rather than an IP address. Likewise, Asus uses router.asus.com. A longer list of these router aliases is on the Introduction to Routers page. In theory, Javascript running inside a web page can use these aliases to access a router.
All that said, should bad guys learn the LAN side IP address of the router, there are still many ways to keep them from interacting with the router. Not using a default password goes without saying, but assorted routers have other defenses such as limiting access to Ethernet connected devices, limiting access by IP address and more. A list of these other defenses is on the Security Checklist page in the LOCAL ADMINISTRATION section.
VLANs top
As if this wasn't enough, you will get still more security with VLANs (Virtual LANs). A VLAN is another subnet. That is, some devices connected to the router might use the 192.168.1.x subnet while at the same time other connected devices might use the 192.168.11.x subnet and still others might use the 192.168.111.x subnet. This is typically done to segment trusted devices away from non-trusted devices (typically IoT). Someone who works from home, for example, might want to insure that no other devices in their home can communicate, or even see, the devices they use for work.
On consumer routers, the Guest Wi-Fi network is probably implemented under the covers as a different subnet from the main network. But, consumer routers don't support real VLANs, for that you need a router with a more techie audience. A long detailed explanation of VLANs is here on the VLAN page.
Router Attacks Based on IP address top
One example of a router attack that depended on its IP address is a bug in D-Link routers that was reported in January 2015 (DNS hijacking flaw affects D-Link DSL router, possibly other devices). Quoting:
"A vulnerability found in a DSL router model from D-Link allows remote hackers to change its DNS (Domain Name System) settings and hijack users' traffic ... Attackers don't need to have access credentials for the affected devices in order to exploit the vulnerability, but do need to be able to reach their Web-based administration interfaces ... Rogue code loaded from a website can instruct a browser to send specially crafted HTTP requests to LAN IP addresses that are usually associated with routers."
The critical point being that using the same LAN IP addresses that everyone else does, makes you more vulnerable to certain types of attacks.
Here is an example of malicious JavaScript attacking modems and routers: Owning Modems And Routers Silently. This type of attack requires the bad guys to guess the IP address of the victim device. If you use a non-standard IP address, you are safer.
The March 2017, WikiLeaks data dump, Vault 7: CIA Hacking Tools Revealed, included a page called JQJDISRUPT - WAG200G that discussed hacking a Linksys router. Of a particular attack, a CIA employee wrote: "it was determined that puppetmon.py was not going to work to get Cannoli on the Linksys target. When running puppetmon.py it eventually always returns errors. User xxx advised that it would only work if the target was in the 192.168.x.x space." The same page describes another attack that only worked if the routers IP address was 192.168.1.1.
Other attacks that need to know (or guess) the internal IP address of the router:
- A JavaScript based attack: Bruteforcing TP-Link routers with JavaScript Feb. 4, 2015. This attack can learn the LAN side IP address of the computer it is running on, so it assumes the router IP address ends with 1. It can be foiled by changing the router password.
- CSRF, Backdoor, and Persistent XSS on ARRIS / Motorola Cable Modems by Tod Beardsley of Rapid7 June 5, 2015. Although the headline uses the term "modem" the vulnerable device is a gateway (modem-router combination). Quoting: "The attacker must successfully know, or guess, the victim's internal gateway IP address".
NOTE: In Jan 2018 this page was drastically re-written. In Dec 2018 many minor changes were made. In November 2020 lots more changes. In September 2024, still more.