Many computing devices need access to the Internet but do not need to interact with any other devices connected to the router. If you have ever used the Internet at a coffee shop, you fit this profile while drinking your coffee. Security increases when devices fitting this profile are prevented from seeing, let alone interacting with, any other devices connected to the same router. In coffee shop terms, this means your laptop is safer if the laptop computers of the other customers can't see it. Bad guys at the coffee shop can't hack into computers that are invisible to their network scans.
For lack of a better term, I refer to this as Network Isolation. Other may prefer to call it network segmentation.
Many devices in your home need nothing but Internet access. Among these would be a Roku box, an Amazon Alexa and an Internet Radio. I have a stereo receiver that can play Pandora and other streaming services. On a home network, the protection offered by isolating these devices is to minimize the impact of a hacked device. Likewise, a malware infested Windows machine can't spread its tentacles, if it can't see any other devices or computers.
A truly isolated malicious device is prevented from learning about the existence of any other devices in the home. It is fooled, by the router, into thinking its the only device connected to the router. All the other devices in the home are thus protected from being spied on. If the CIA hacks your smart TV, the router prevents the TV from seeing anything you do on your computer.
To be clear, allowing a wireless device to access nothing but the Internet means:
- Isolated wireless devices can not see other users/devices logged on to the same Wi-Fi network (a.k.a SSID)
- Isolated wireless devices can not see users/devices on other Wi-Fi networks created by the router
- Isolated devices can not see any device connected via Ethernet to the router
- Isolated devices can not directly access the router. Even if they know the userid/password to logon to the router, they are prevented from loading the routers logon web page
Truly isolated devices run inside a VLAN. Specifically, a VLAN that does not allow communication with other VLANs.
A VLAN is a virtual LAN. A network within a network. A logical (not necessarily physical) grouping of devices.
VLANs were not initially created for the type of network isolation I advocate here. As such, there is a configuration option for each VLAN that controls whether it is allowed to communicate with other VLANs or not. In addition, there is another configuration option that controls whether the devices in a VLAN can see and communicate with each other.
As an analogy, consider a pet store with many fish tanks full of fish. Since the fish in one tank can not interact with the fish in another tank, each tank can be thought of as a VLAN that does not allow communication with other VLANs. A better analogy would be if each tank had a curtain around it preventing the fish from even seeing any of the other tanks.
Devices that only need Internet access, are best isolated in a fish tank by themselves. They can't see the other fish tanks (VLANs) and they can't see any other fish (computers).
But, sometimes we do need the fish in a tank to interact with each other. If, for example, you want to use a mobile device to control a Roku box, then both devices have to be able to communicate. The same with Sonos speakers that can also be controlled by a mobile device. I am told that Chromecast is another example, as a mobile device needs to see the Chromecast to set it up initially.
The most secure setup would be to put the Roku, Sonos and Chromecast devices in their own VLANs, configured to allow the devices/fish to see other, and assign a single SSID to each of those VLANs. Then, when a mobile device needs to communicate with the Roku, for example, it logs into the dedicated Roku SSID. This is annoying, but security and convenience have always been enemies. Also, you may run out of SSIDs. Prior to firmware version 8, the Surf SOHO could create only three SSIDs. As of firmware 8, it can create 16.
If a particular device, such as a Roku box, can be totally isolated most of the time and only rarely needs to communicate with another device in your home, then you might have it totally isolated by default and just enable sharing within its VLAN on the rare exceptions when you need it (thanks to Zach for the idea). Of course, disable sharing when you are done.
Before leaving the fish tank analogy, any time the fish in a tank are allowed to see and interact with each other, a big fish may eat a small one.
ISOLATION WITHOUT VLANS
VLANs are only offered in professional grade routers. With consumer routers, there are two approaches that approximate VLAN segregation: Guest Wi-Fi networks and using two routers.
A Guest Wi-Fi network is somewhat isolated from the main network. I say "somewhat" because the isolation varies and may be configurable. The vast majority of consumer routers offer a single Guest network; some offer one on each Wi-Fi frequency band (2.4GHz and 5GHz). In contrast, a router that supports VLANs will probably let you create dozens of them. Also, Guest networks are Wi-Fi only, VLANs can also exist on wired Ethernet connections.
To illustrate how the isolation offered by a Guest network varies across vendors: when configuring a Guest network on a TP-Link router (screen shot) there is a checkbox for "Allow guests to see each other". TP-Link Guest networks also have a checkbox to "Allow guests to access my local network." Google Wi-Fi has no hard barrier between the Guest and private networks. The system supports shared devices, a feature that can not be disabled. Asus offers a choice as you can see here. I am pretty sure that the "Access Intranet" option breaks down the wall between Guest and private devices. Netgear is confusing. Their article How do I set up a guest network on my Nighthawk router? says nothing about this, but others have seen an option to "allow guests to access my local network" This PC Magazine article has a screen shot of a Netgear router with an option to "Allow guest to see each other and access my local network." Eero has no sharing options for a Guest network. Trendnet has two options: "Wireless client isolation" and "Internet Access Only". The Synology RT2600ac offers two Guest networks, but they share the same subnet, so they are not isolated from each other. You can learn more about Synology Guest networks in my review. D-Link has an option to "Enable routing between Zones" which you can see in this screen shot from this 2016 Gizmodo article.
Peplink does not offer Guest Wi-Fi networks per-se, but it does offer two isolation options. To prevent devices on the same Wi-Fi network (SSID) from seeing each other, you can enable "Layer 2 isolation". If a Wi-Fi network is assigned to a VLAN, you can isolate that VLAN from all other devices connected to the router by disabling "Inter-VLAN routing."
The other option, using two routers, should offer total isolation. In this case, you connect the WAN/Internet port of the inner router to a LAN port of the outer router. The outer router is either connected to a modem or is a combination modem/router device. The firewall of the inner router isolates devices connected to it from all the devices connected to the outer router. For someone working from home this is a fairly secure way to isolate their work devices from everything else in the home. One downside to this approach is that it does not scale. Another is that there will be no option to isolate devices connected to the inner router from each other. On the upside, it isolates Ethernet-connected devices, something Wi-Fi can not do. For more on this, see my September 2020 blog A second router can make working from home much more secure.
SIMPLE AND COMPLEX VLAN EXAMPLES
The fish tank in the previous analogy can be thought of as the boundary or scope of a VLAN. Stepping out of the analogy, the scope of a VLAN actually consists of Wi-Fi networks (SSIDs) and Ethernet ports. On the simplest level a VLAN can consist of a single SSID or a single Ethernet LAN port. You can mix and match too.
- An easy way to start with VLANs is to assign an SSID to a VLAN
- Another simple setup is to assign a LAN port to a VLAN that consists of just that one port
- As a next step, you could take multiple LAN ports and group them into a VLAN
- Or, you could put some Ethernet ports and an SSID into the same VLAN
- The most complex setup involves a VLAN enabled smart switch, plugged into a LAN port
Type 1 is basically a Guest Wi-Fi network on steroids. The devices using that SSID will be walled off from all other devices connected to the router (assuming that inter-VLAN routing is not allowed). You might use one such isolated SSID for actual guests/visitors and another one for IoT devices such as a Roku box, an Apple TV, an Amazon Echo, a Nest thermostat or an Internet radio. This way you can change the Guest network password without impacting the IoT devices. And, the Guest network can be disabled when its not needed.
As an example, of Type 2, I use a VOIP service that provides a small telephone adapter box. One end plugs into a LAN port on my router and the other end plugs into a land-line telephone. The Ethernet port used by the telephone adapter is in its own, really tiny, VLAN.
Roommates could use Type 4. Each person could have their own SSID and two LAN Ports assigned to their personal VLAN. In effect, this chops the router in half and never the twain shall meet. Likewise, someone who works at home could use type 4 as a way to isolate the computers/printers/etc that are used for work from all the other devices in their home. Someone who works at home and wants the best possible security might use type 3 and limit themselves to 2 or 3 LAN ports and avoid Wi-Fi altogether.
OVERKILL?
Are VLANs overkill?
- It has been suggested a billion billion times to use a VPN on public Wi-Fi networks. But, VPNs offer no protection from malicious devices on the same Local Area Network (LAN). Neither does TOR. Windows machines, especially, have a history of being compromised by a LAN side attack, no Internet needed. The WannaCry ransomware attack in May 2017 was an example of this.
- Firewalls protect devices on a LAN from outside attack. The Network Isolation I am suggesting here protects devices on a LAN from inside attack. For more on testing the firewall in your router see the Test your router page.
- If you have done an NMAP scan of all 65,500 (or so) TCP ports, and another scan of the 65,500 (give or take) UDP ports that your laptop or tablet might have open to the LAN, and, you can explain and understand what each port is doing, and you are not worried about bad guys in the coffee shop abusing the service behind these open ports, then it is overkill. Everyone else would benefit from Network Isolation.
VLANs IN THE NEWS
Need some convincing before bothering with VLANs? See some stories in the news about bad things that a VLAN would have prevented.CREATING A VLAN
April 27, 2024. ASUS: This page describes creating a VLAN using a Peplink router. In my opinion, the process is fairly simple. This article from Asus: What is VLAN and how to setup in ASUS Wireless Router? (April 18, 2024) describes the process on their routers.
I found it incomprehensible. Asus has invented their own terminology that is not well explained. And, its not even meant to be an explanation of anything, it is just a click-here, type-this thing for a robot to follow. Also, something is also lost in the translation to English. The first thing they discuss is trunk ports and access ports. New VLAN related terms (to me at least):
port isolation, VLAN profiles, VLANs without DHCP, VLAN-only-network. As of now, VLANs are only supported on 6 Asus models. It's not clear if VLANs are in Beta status for some of these models or for all of them. Nothing is clear at all.
- - - - - - - - - -
The first thing you do with a VLAN is create it, which means giving it a name, a number and a subnet. After a VLAN is created, it is then assigned to one or more wireless networks (SSID) and/or one or more Ethernet LAN ports. The final step, which is optional, is to create rules for communication between VLANs.
The process for creating a VLAN on Peplink routers is below. This was last verified on a Surf SOHO running firmware 8.2 and a Balance 20x running firmware 8.3.
- The process starts at the Network tab -> Network Settings (in the left side vertical column). The LAN section of this page shows the existing VLANs, if any, and also has an entry for the untagged LAN. Click the gray New LAN button. If you are thinking that the label of the button leaves something to be desired, you are correct.
- The VLAN name and number are arbitrary. Some useful names might be IoTvlan, VOIPvlan, HarveysVLAN or GuestVLAN. Some useless names are GeorgeWashington and LetsEachLunch.
- VLAN numbers (the field is called VLAN ID) should be between 2 and 4,094. Like the name, this too can be arbitrary, but you may want to be neat and use a number that is related to the next field, the subnet. My experience has been that Peplink routers always show you both the VLAN name and number so there is no need to memorize the number.
- Each VLAN gets its own subnet. The subnet can be any internal-use-only subnet (192.168.x.x or 10.x.x.x most likely) that is not already used on the router. So, if the main LAN (untagged LAN to be precise) was using 192.168.5.x, then the first VLAN could be 192.168.6.x. A second VLAN could be 192.168.7.x. If you do this, then consider assigning a VLAN number of 5 to the one using the 192.168.5.x subnet and use number 6 for the VLAN with the 192.168.6.x subnet. Not a requirement, just neat. The third VLAN could use subnet 10.7.7.x and be assigned VLAN number 7. Just a suggestion. For more on subnets, see the IP address page.
- If you are creating the VLAN to totally isolate devices, then be sure that the checkbox for Inter-VLAN routing is off. If you allow Inter-VLAN routing, then you probably want to configure some internal firewall rules to control this.
- I prefer to enable DHCP logging. It is not a big deal, but I sometimes find the log of when devices connected to the router useful. As of firmware 8.3, the DHCP log has its own tab so it no longer clutters up the main event log.
NOTE: If you assign a Wi-Fi network to a VLAN, the Wi-Fi password does not change.
NOTE: VLANs do not get their own passwords. Ethernet ports that are assigned to a VLAN are not password protected. You do not assign a MAC address to a VLAN, just 1 or more LAN ports and/or 1 or more SSIDs.
An interesting thing about each VLAN being its own subnet, is that the router itself has multiple LAN side IP addresses. For example, from the 192.168.7.x subnet, the router might be assigned to 192.168.7.11 (a lucky number). At the same time, on the 10.11.12.x subnet the router might be assigned to 10.11.12.13 (easy to remember). How you access the router, depends on which subnet/VLAN you live inside. For security, Peplink can block all subnets except one (you choose which one) from being able to access the router at all from the LAN side. You certainly don't want a smart garage door opener to be able to login to the router :-)
In addition to assigning the router an IP address in a VLAN subnet, you also define the range of IP addresses that DHCP will give out in that subnet. Each subnet is independent so this range can vary. For example, you might give out 192.168.7.12 through 1921.68.7.250 while at the same time giving out 10.11.12.20 through 10.11.12.222.
But wait, there's more ... you can also assign DNS servers that will be used by devices in the subnet (and thus in the VLAN). Too lazy? Fine, all subnets/VLANs can use the same DNS servers. Your choice. If you put devices used by children into a VLAN, then that VLAN can use DNS servers that block porn.
NOTE: IF DNS forwarding is enabled in the Surf SOHO, then the router forces all old-style DNS queries to be answered by the router itself. This over-rides the DNS servers specified for a VLAN. Newer, encrypted DNS requests from router clients, specifically DoT and DoH, bypass the router entirely.
A common first problem after implementing VLANs is printing. Specifically, how do devices in a VLAN get to a shared network printer? Since this breaks some of the isolation that VLANs can offer, this topic is at the bottom of the page. It's also covered last because it's complicated.
VLAN SUPPORT
Many routers can offer some isolation but the feature is often disabled and limited in scope.
Support for VLANs is rare. I have not seen it in any consumer routers. None of the consumer oriented mesh routers support it. My recommended router, the Pepwave Surf SOHO, fully supports VLANs, but it is an advanced feature and disabled out of the box. You have to know a secret handshake (see below) to enable VLANs on the Surf SOHO.
The high end Synology RT2600ac, which seems to offer every feature ever invented for routers, does not support VLANs (according to the user guide for SRM version 1.2)
August 13, 2022: I am told that there is VLAN support in SRM version 1.3.something
The isolation offered by the RT2600ac is a hodgepodge. On a non-Guest network, devices may or may not be able to communicate with each other depending on an AP Isolation option. The manual does not address sharing between Ethernet devices and non-Guest Wi-Fi users. On a Guest network, devices on the 2.4GHz band can not see devices on the 5GHz band. The manual wasn't clear as to whether AP Isolation was available for Guest networks within one frequency band. And, like many routers, Guest devices can access non-Guest devices if you so choose.
I don't mean to downplay Guest networks, they are a great security feature, even without full network isolation. Having a different password from the main Wi-Fi network lets you periodically change the password so that Guests don't get a permanent pass. Guest networks can also be disabled when they are not needed. And, they can offer some isolation of Guest users/devices.
That said, many consumer routers offer just one guest network and I don't think that's enough. For example, I suggest having one Wi-Fi network for devices that need to see other devices, one for actual guests or visitors and another for IoT devices. Parents with small children, may also want to isolate devices used by the kids.
THE TOTAL REVERSE
While this page focuses on giving a computing device access to the Internet and nothing else, sometimes we need the reverse. That is, we want a device to be accessible locally but not have access to the Internet. The firewall in any router should prevent incoming access from the Internet, at least as long as UPnP is disabled. A router that supports firewall rules, will let you block the device from making any outgoing connections to the Internet. No phoning home for ET. Needless to say, my preferred router, the Pepwave Surf SOHO, supports outbound firewall rules. Generally speaking, consumer routers do not offer outbound firewall rules.
PEPWAVE SURF SOHO VLANs
To use VLANs on the Surf SOHO, you first define a VLAN (or two or three) and then you give the VLAN(s) a scope. By scope, I mean assign the VLAN to an SSID (Wi-Fi network) and/or an Ethernet LAN port. A VLAN that is defined but not assigned to anything can be deleted. A VLAN that has been assigned to either an SSID or a LAN port (or both), can not be deleted. The creation of VLANs starts at Network -> Network Settings (shown below).
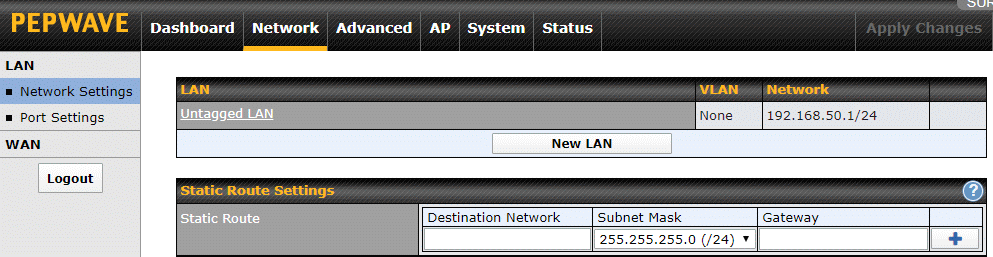
Before creating new VLANs, there are two changes I suggest making. As noted earlier, VLANs were not created for total network isolation and, by default, at least with Peplink routers, communication is allowed between different VLANs and non-VLAN devices (that is, stuff on the untagged LAN). So, click on "Untagged LAN" and turn off the "Inter-VLAN routing" checkbox. This will prevent devices that are not part of any VLAN (untagged devices) from any and all communication with whatever VLANs you create.
Next, I would give the "Untagged LAN" a more descriptive name. This is the default name for the group of devices that are NOT in any VLAN. The default name is technically correct; chunks of data (called packets or frames) transmitted on a network with VLANs have an extra tag that identifies the VLAN each chunk/packet/frame belongs to. Devices that are not part of a VLAN do not have their network packets tagged. I suggest changing the name just because it is not helpful for people who are not experts at networking.The name you choose can be anything that makes sense to you. Consider something like PrivateLAN or PrivateNetwork or MikeysPrivateLAN. Then click the gray Save button at the bottom of the window and, again, Apply Changes.
In Firmware 7, support for VLANs was disabled out-of-the-box. In firmware 8, the ability to create VLANs is enabled by default.
Firmware 7 only: To enable VLAN support do Network -> Network Settings. In the "IP Settings" section at the top of the page, click on the white question mark in the blue circle. A small window pops up saying "If you need to define multiple VLANs, press here". Click on the word "here". A second window pops up that says "The LAN settings will be switch to advanced mode with VLAN support. Are you sure?" CLick on the Proceed button. Then, click on Apply Changes. This takes you back to the main Dashboard page.
Go to Network -> Network settings again. The gray button labeled "New LAN" really should say "New VLAN". Click the "New LAN" button to define a new VLAN and you will see the screen below (it looks exactly the same in firmware 7 and 8).
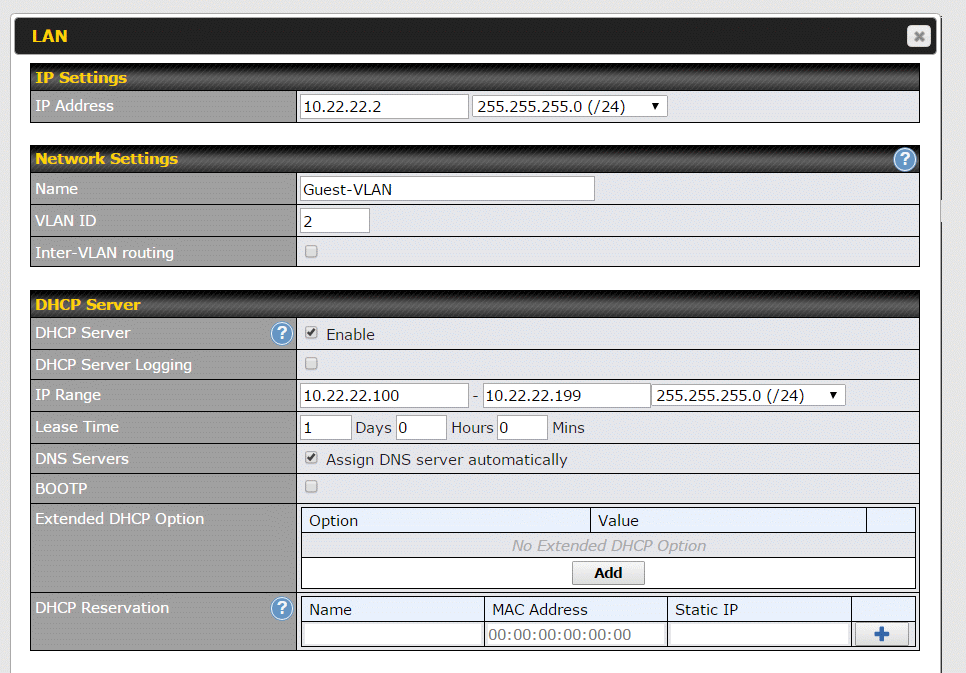
Previously I mentioned that each VLAN gets its own subnet (sub network or range of IP addresses), name, number and DNS servers. This is where we assign these attributes. It is also where we control whether the VLAN can talk to other VLANs and whether devices in this particular VLAN can see each other. Assigning most of these attributes is easy, assigning the subnet requires some techie knowledge.
The first field (IP Address) is not one I mentioned before. It is the IP address of the router, as seen from this VLAN. This is part of defining the subnet that the VLAN will use. In the example above, the VLAN is using the 10.22.22.x subnet. This means that all devices in that VLAN will have IP addresses that start with 10.22.22. All devices. Even the router itself. The first field is where you give the router an IP address in the new subnet used by the new VLAN. In the screen shot above, it is device number 2. For nerds, this is interesting. From the main network (untagged LAN), the router is addressed as 192.168.50.1 (using Peplink defaults), but from this new VLAN/subnet, it will be addressed as 10.22.22.2.
Why 2? Why not assign 10.22.22.1 to the router? Most people use 1. It is best to avoid an IP address that ends with 1 or 254. For more on this, see the IP address page.
The field next to the router IP Address is complicated. However, the value shown (255.255.255.0/24) should be fine in almost all cases. It means that the subnet used by this VLAN can have a maximum of 255 devices (numbered 0 through 254). If nerds ask, this is a subnet mask.
Another subnet related field is the "IP Range" in the DHCP Server section.
All computing devices on a network need a unique number. Here we are dealing with IP version 4 numbers/addresses. Devices can either be configured to always use a specific IP address/number or be assigned one on a temporary basis when they join a network. Most of the time, devices use temporary IP addresses assigned by the router. The router itself is an exception, it has a fixed, static IP address that we just configured. The system that loans out temporary IP addresses is called DHCP.
In the example above, devices that don't have a fixed IP address will be assigned one ending in 100 through 199 (10.22.22.100 through 10.22.22.199). This implies that we can use fixed/static IP addresses between 1 and 99 and between 200 and 254 for devices that need one that never changes. A network printer, for example, is best assigned a fixed IP address. This range of temporary IP addresses was an arbitrary choice, it could just as well have been 100-250 or 30-252. The lowest number can not be lower than the number given the router. The highest number is 254.
That's the hardest part. Now, it gets easier.
The name of the VLAN goes in the Name field (see, easier). In the example, the name is Guest-VLAN. The name should be whatever makes sense to you based on who or what will be using this VLAN. If you intend to use the VLAN with a single SSID, then perhaps name it after that SSID. For example, the VLAN for SSID "michael" might be called "michaelsvlan". A VLAN for IoT devices might be called IoTvlan. Personally, I have a VLAN that consists of a single Ethernet LAN port used by a VOIP telephone adapter. I call it VOIPvlan. It is not clear how long the name can be or what characters are allowed/disallowed, so don't go crazy.
In addition to names, VLANs are also assigned numbers. The important attribute of the number seems to be that it is unique. Peplink refers to the number as a "VLAN ID" but its a number.
The number does not have to be related to the subnet, but being neat simplifies things. For example, you might assign the VLAN using the 10.2.2.x subnet number 2. Or, if you like 192.168 subnets, then consider assigning the number 4 to the 192.168.4.x subnet and 8 to the 192.168.8.x subnet. VLAN numbers do not have to start at 1 and do not have be consecutive. In the Peplink manual they name the VLAN after its number. VLAN number 2, for example, is called VLAN2. Boring.
The next field, "Inter-VLAN routing" is why you are reading this page. Turn this off (it is on by default in firmware 8). With this disabled, devices in this VLAN can not access anything outside of their VLAN. Even if some other VLANs want to share stuff, this VLAN will not come to the sharing party. Disabling this does not block access the Internet.
I suggest enabling the DHCP server and DHCP Server logging. These can always be changed later. A Lease Time of one day (the default) should be fine. This is how long a device can use an IP address before it has to go back to the router and ask for another one. The Surf SOHO has been giving the same device the same IP address for years now, but that may change in the future. Opt to assign DNS servers automatically and do not check Bootp. There is no need to deal with the Extended DHCP option or DHCP Reservation.
When done, click the SAVE button at the bottom of the window and then Apply Changes, yet again.
To assign our newly minted VLAN to an SSID, go to AP -> Wireless SSID and click on the SSID name. As shown below, click on the drop down list box in the VLAN ID field. VLANs are identified here both by name and by number.
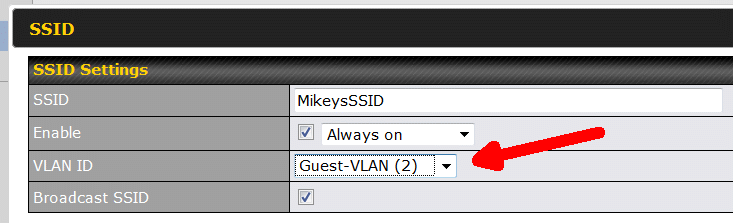
At this point, you do not see the option that isolates devices on this SSID/VLAN from each other. The router defaults to a simple mode and you need to know the secret handshake to see the advanced settings. As shown below, the secret handshake is the white question mark in the blue circle. You need to click it, and then click again, where instructed (see below).
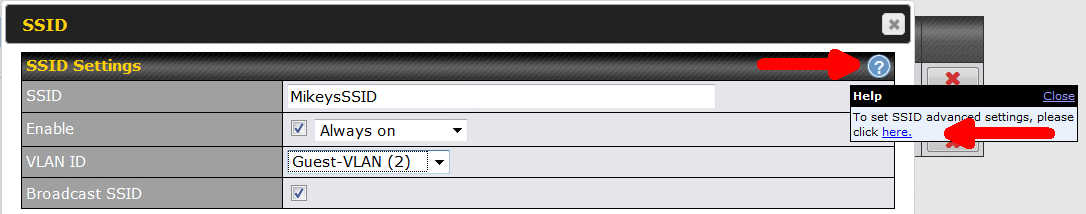
Now you should see a checkbox for "Layer 2 isolation" as shown below. This is what isolates devices within this one VLAN/SSLID.
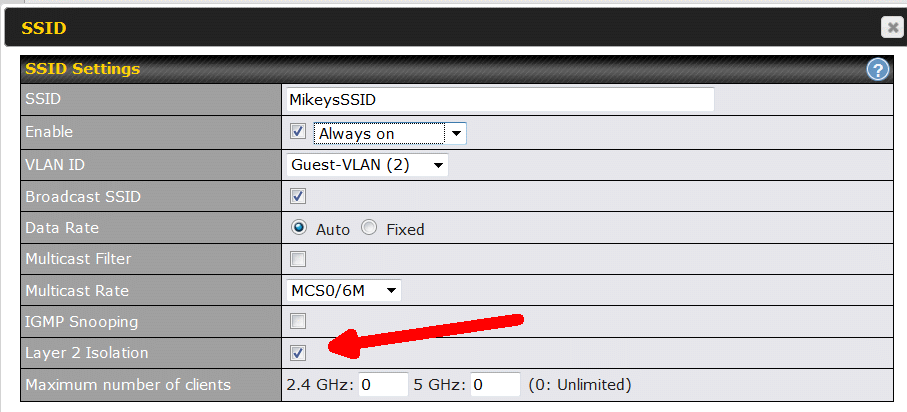
Be sure to click the Apply Changes button on the top of the screen, when you are done making changes.
At this point, you have a single, totally isolated, SSID. Congratulations.
NOTE: While VLAN isolation applies to all devices in a VLAN, Layer 2 isolation is a Wi-Fi thing, not a VLAN thing. This means that in a VLAN with both wired and wireless devices, the wired devices are able to see the wireless ones. I have not tested the reverse ....
The Surf SOHO allows for more than one isolated SSID. Simply create another VLAN for the second wireless network. The Surf SOHO can create a maximum of eight SSIDs.
ETHERNET PORTS
When assigning Ethernet ports to a VLAN, you are presented with a choice - whether the LAN port is "Access" or "Trunk". Access mode used to be the default, as of firmware v8, Trunk is the default.
Recall from earlier, that network packets that are part of a VLAN are "tagged" with the identifier of that VLAN. The private LAN is also called the "untagged LAN" because data packets have no VLAN tag on them.
Now, consider a LAN port that is assigned to a VLAN. Does the router have to add the VLAN tags as data packets come into the LAN port or is the device connected to the LAN port already providing the VLAN tagging? That is the issue that "Access" and "Trunk" address.
"Access" means that the incoming data has no VLAN tags so the router has to provide them. Most devices plugged into an Ethernet LAN port (laptop computer, desktop computer, VOIP telephone adapter, network printer, stereo receiver, Roku box) do not understand VLANs so the responsibility of tagging stuff falls to the router.
A device that does understand VLANs would be a smart switch. Smart switches are step up from dumb switches and a step down from a router. When a smart switch is plugged into a LAN port, then the type should be Trunk. This tells the router not to bother adding VLANs tags, the smart switch has already done so.
The Netgear GS105E is a smart switch with 5 Ethernet ports and VLAN support. It cost about $40 in January 2018 and from $40 to $55 in March 2020.
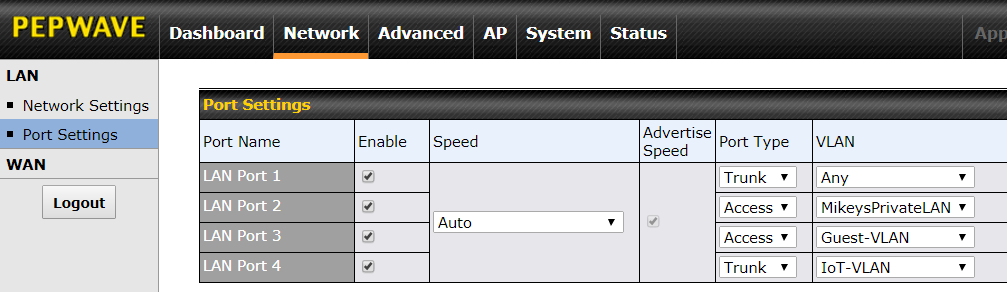
Below is the Peplink user interface for assigning different VLANs to different LAN ports. Anything plugged into LAN port 3 will be assigned to the Guest VLAN and anything plugged into LAN port 2 will not be assigned to any VLAN. I use "MikeysPrivateLAN" as the name of my non-VLAN untagged network. An Ethernet-only network printer would belong in LAN port 2.
TRUNK ports are more complicated. The smart switch plugged into a TRUNK port can send data for multiple VLANs, depending on how the switch is configured. But, the router is not bossed around by the smart switch. You can control which VLANs the router will accept from the smart switch. In the screen shot below, LAN port 1 allows the smart switch to send data for any VLAN, while LAN port 4 will only accept data for the IoT VLAN from the smart switch that is plugged into it.
FINAL NAIL
The final nail in the total isolation coffin, is limiting the VLANs that can login to the router's web interface. For the best security, restrict router access to the private network. That is, prevent all VLANs from having direct access to the router.
To do this, go to System -> Admin Security -> Allowed LAN Networks (see below).
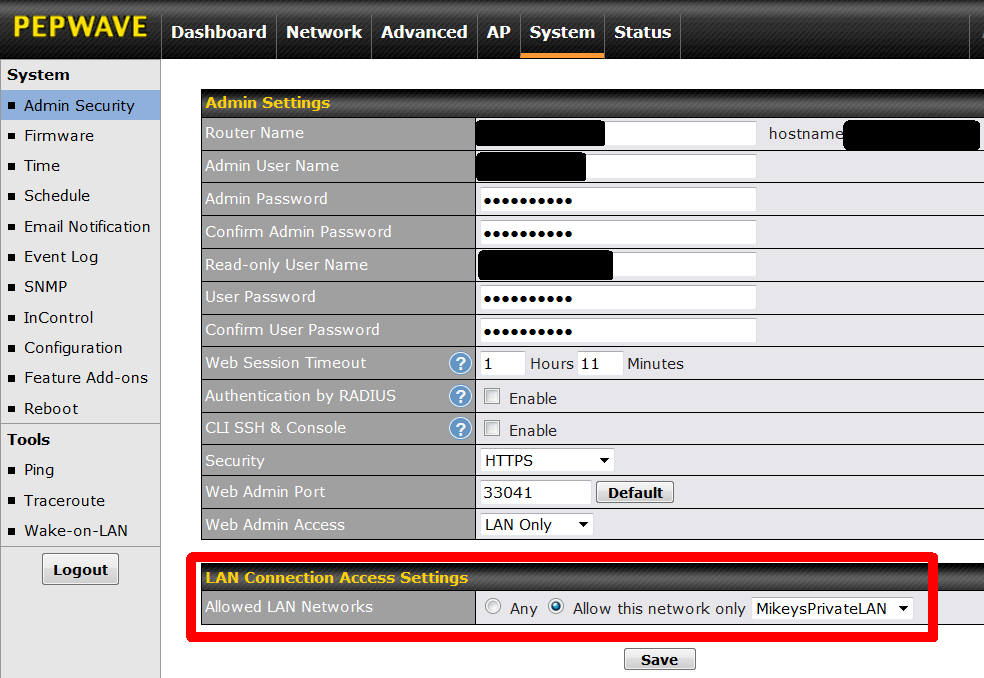
The "Allowed LAN Networks," defaults to Any which means users on all VLANs can login to the router. In the screen shot above, this has been changed and only MikeysPrivateLAN is allowed access to the router. Continuing the earlier example, this prevents anyone on the 10.22.22.x subnet/VLAN from logging on to the router using IP address 10.22.22.2. They won't even be able to view the logon page. After changing this, click the SAVE button, then the APPLY CHANGES button.
Continuing with the previous screen shot, the one in the Ethernet Ports section above, this means a computer plugged into LAN port 2 (MikeysPrivateLAN) can access the router, while one plugged in to LAN ports 3 (Guest-VLAN) and 4 (IoT-VLAN) can not.
Interestingly, this setting also blocks the Peplink mobile app from talking to the router, if the app connects to an SSID/VLAN that is not allowed in. Learned that the hard way.
PRINTERS (Added: April 11, 2021 | Updated: Oct 9, 2021 and March 27, 2022)
Shared devices, such as network printers, can be a problem after setting up VLANs for isolation. In the simplest case, a shared network printer is on the untagged LAN and so are all the devices that need to print. But, once you want to print from a device in a VLAN, things get complicated.
One solution is to move the device that wants to print to the untagged LAN, temporarily, and then move it back to its VLAN afterwards. If the device is Wi-Fi, then it needs to disconnect from the SSID assigned to its VLAN and connect instead to an SSID assigned to the untagged LAN. If the device is Ethernet-connected, then it either needs to be plugged into a different LAN port (one assigned to the untagged LAN) or the LAN port it is using, needs to be re-assigned to the untagged LAN, temporarily.
Another solution is to put the printer into its own dedicated VLAN, one used just by the printer and nothing else. This printer-only VLAN should allow incoming requests from router clients but be blocked from making outbound requests. We block it in case the printer is malicious. To set this up:
- Create a VLAN for the printer and enable inter-VLAN routing for it. Also, assign the printer a static IP address in its VLAN subnet.
- Every VLAN that wants to access the printer, needs to have inter-VLAN routing enabled
- If the untagged LAN needs to access the printer, then inter-VLAN routing needs to be enabled for it too
- If the printer connects via Ethernet (best case), assign the printer VLAN to a LAN port of type ACCESS (not TRUNK)
- If the printer connects via Wi-Fi create a new SSID for the printer and assign the SSID to the printer-only VLAN
- At this point, try to get your devices to print. The steps below lock things down more but configuring your devices, even at this step, may take some doing. On Windows 10, I have read that you need to assign the printer to a TCP/IP port.
- To block the printer VLAN from communicating with the Internet, create an outbound firewall rule. That said, there may be times when you want to update the printer firmware, so this rule will need to be temporarily disabled to allow the printer to phone home for new firmware.
- Inter-VLAN routing defaults to allowing all traffic between VLANs (and the untagged LAN too). At this point we create some Internal network firewall rules to lock things down more. On a Surf SOHO running firmware 8, these rules are at Advanced tab -> Access Rules (under Firewall) -> Internal Network Firewall Rules. On a Balance 20x running firmware version 8, the rules are on the Network tab, also under Access Rules.
- One rule blocks the printer VLAN from initiating any outbound communication to other devices attached to the router. We want the printer to accept incoming requests only.
- Another rule can block devices from being able to access the administrative interface of the printer. For example, if the printer has an internal webserver that listens on port 80, then block all the VLANs that can access the printer VLAN from sending any port 80 requests to the printer. Or, maybe, just let one VLAN send port 80 requests and block the others.
- Optionally, limit inbound traffic to the printer to just the ports that are needed for printing. This is hard, because printers support different types of communication which use different TCP/IP ports. Which ports? I ran a TCP port scan on my Canon network printer and found these ports open: 443, 515, 631 (IPP), 9100 (jetdirect) and 8610 (canon-mfnp). In addition, I had created a custom port for web access to the printer, and that was open too.
To expand on the last point above, I am no expert at printer communication. One person told me that all he needed was port 443. I ran one test, printing from Notepad on a Windows 10 computer. A pcap trace with Wireshark showed the PC communicating with the printer on TCP port 443 (a TLS connection), TCP port 9100 and UDP port 8610. No doubt the ports used for printing will vary by operating system, by printer driver and probably with the application software too.
There are a number of items on the Peplink Forum about shared printing with isolated VLANs. This is not something I have personally dealt with. The steps above come from the Peplink Forum item called Guide to setting up VLANs for Printing with Firewall isolation by Marcus Dowling. I have expanded on it a bit. The examples there assume the use of InControl2, but the concepts are the same without it.
ASSORTED POINTS
The competition: Creating Isolated Networks with Ubiquiti UniFi by Christian Mohn (August 2019). Ubiquiti has two VLAN configuration options, Network purpose and Network Group, that its not clear to me what they are/do. Ubiquiti can not assign names to VLANs. Isolating a VLAN requires firewall rules rather than a single checkbox.
The competition: Mike Potts documented on GitHub Using the Ubiquiti EdgeRouter X and Ubiquiti AP-AC-LR Access Point to create VLANs for each of 3 LAN ports and three different SSIDs. Here is an overview in PDF format. The heart of this is a 105 page PDF document with the full instructions. Compare that to this page. Seems much more complicated than the Surf SOHO (or any Peplink router). For example, look at all these firewall rules. Ugh. The EdgeRouter X is about $50 and the Access Point is about $100, so its roughly $50 cheaper than a Surf SOHO. That said, there are many costs other than financial. For example, Mr. Potts said "The only trouble with this router is that it is meant for professionals to use. You have to scrounge around forums for postings on how to configure specific items." Peplink routers are also targeted at professionals, yet the user interface is fairly easy to use.
A Pepwave Surf SOHO limitation: This Feb. 2019 Forum question asks: "I have segregated printers into a separate VLAN. To make them broadly accessible from other VLANs with iOS devices (etc), I need to enable Inter-VLAN Bonjour ... How do I enable Bonjour on the SOHO MK3?". You can not. Bonjour forwarding is only supported on the higher end Balance and HD routers.
- - - - - -
EXTRA CREDIT
This is unlikely to happen often, but understanding the question shows a good grasp of things.
A regular switch (as opposed to a smart switch or a managed switch) is a relatively dumb Ethernet-only device that takes chunks of Ethernet data (packets/frames) in on one port and sends it out another port. Conceptually, a switch is the opposite of the network isolation described above on this page. Rather than prevent devices from seeing each other, it always lets all connected devices see each other. That's its job. That's why people buy switches. So, what do you think happens when worlds collide?
Suppose the Surf SOHO has a LAN port port assigned to an isolationist VLAN. That is, the VLAN has Layer 2 Isolation enabled and it is not allowed to talk to any other VLANs. Any device directly plugged into that LAN port can only see the Internet. It will be blissfully ignorant and shielded from other devices using the router. That's easy.
But, what if you plugged a switch into that LAN port? What then of the devices plugged in to the switch? Can they see each other as per the switch or can they not see each other as per the router and the isolationist VLAN assigned to the LAN port? When the router and the switch arm wrestle, who wins?