NOTE: A config file from the 2nd generation of the Surf SOHO can not be used on a 3rd generation model.
Until I have a spare third generation model, this page is useless.
This page is also incomplete as I learned this while creating the page.
There is a long description on this site of the Pepwave Surf SOHO router. There is also a long page describing the initial configuration of the router. This page exists to offer a downloadable configuration file for the Surf SOHO. For anyone new to the router, this can serve as a more convenient starting point.
==> Download Configuration file <==
The configuration file was created using firmware version 8.1.3 which was the latest in September 2021 when it was created. It should not be used with older firmware.
More importantly, it was created on a second generation Surf SOHO (HW2) and thus should only be used on a second generation model. It should not be used with the third generation (MK3) models.
It is always best to save the current configuration before uploading a new one. To do this go to the System tab -> Configuration -> Download Active Configurations.
This configuration will certainly work for LAN side access to the router. However, it has default values for the Internet connection, so you will have to change the WAN options. The one parameter I changed is to force the Internet connection to use Quad9 for DNS (9.9.9.9 and 149.112.112.112) rather than DNS servers from the ISP.
Getting access to the router initially is described on the initial configuration page. To install this sample/starter configuration:
- Go to the System tab
- Click on Configuration in the left side vertical column
- In the Upload Configurations section, click the gray Browse... button and navigate to the downloaded configuration file
- Finally, click the gray Upload button and wait for the router to reboot
To access the router, with this configuration, from the LAN side:
- The IP address of router is 192.168.55.5
- Access is limited to HTTPS (no HTTP)
- The port number is 22555
Putting this all together, the URL is: https://192.168.55.5:22555
Remote access to the router if off. The DHCP range is 192.168.55.10 through 192.168.55.240
LOGGING IN
To login to the router, the admin user is "baberuth" and the admin password is "1927newyorkYankees". There is also a read-only user defined. The userid is "readuser" and the password is "23baseballBATS".
After logging in as Babe Ruth, the dashboard will look like this:
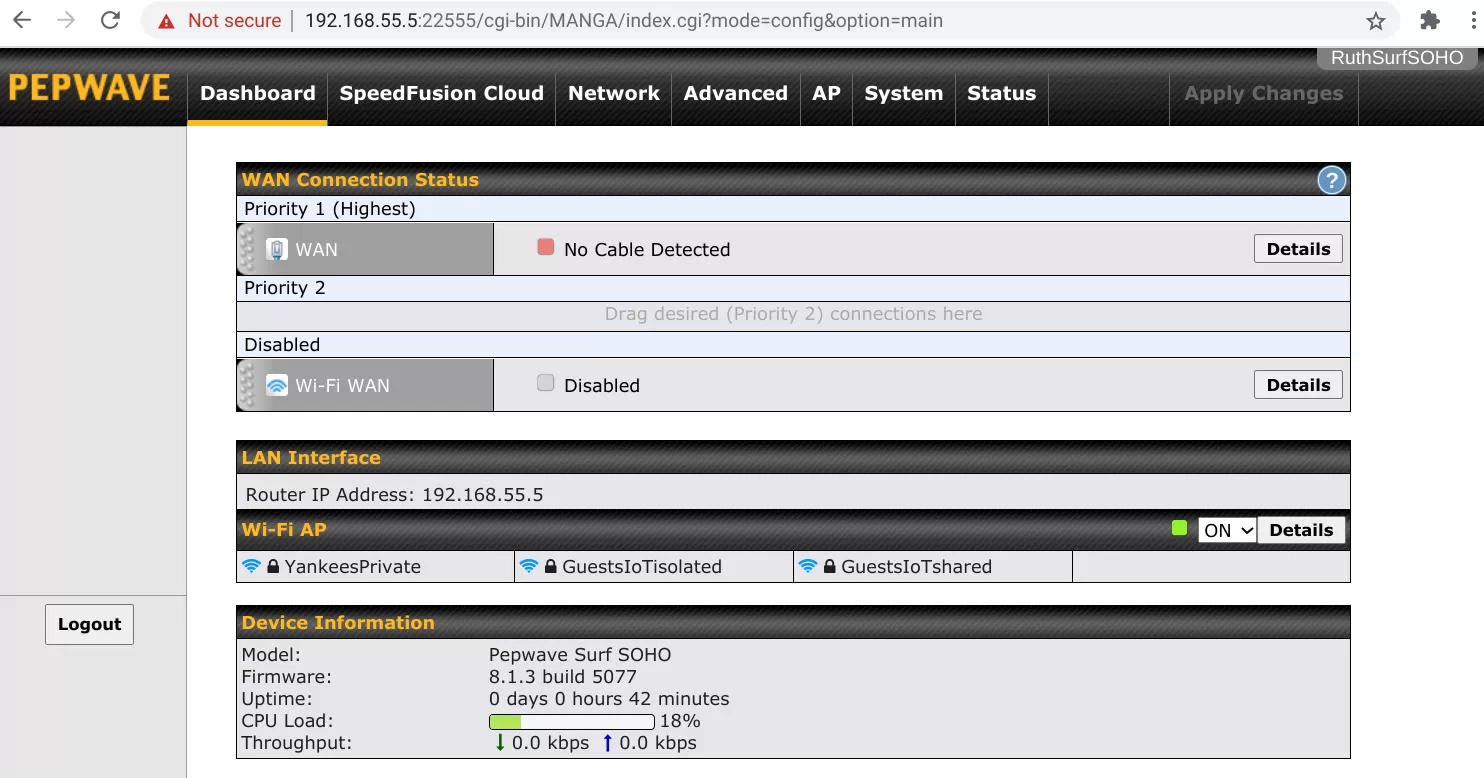
WIFI
As shown above, there are three Wi-Fi networks (SSIDs). They all use WPA2 Personal.
NAME: yankeesprivate PASSWORD: 88greenlightBULBS88
This is the private network and it is shared with all the LAN side Ethernet ports. The subnet is 192.168.55.x.
NAME: GuestsIoTshared PASSWORD: 44Yellow44basketballs
This is for both IoT devices and Guest humans. Devices on this SSID are allowed to see each other. This is assigned to VLAN number 11 and the subnet is 10.11.11.x.
NAME: GuestsIoTisolated PASSWORD: 77redbaseballCAPS77
This too is for both IoT devices and Guests. However, devices on this SSID are not allowed to see each other. This is assigned to VLAN number 22 and the subnet is 10.22.22.x.
Actual Guests (people) belong in the GuestsIoTisolated SSID. Whenever possible, put IoT devices there too. If, however, you need to communicate with an IoT device over the LAN, then that device needs to be in the GuestsIoTshared SSID. Neither of the Guest/IoT networks can see anything in the private network. They are also blocked from access to the router.
The Wi-Fi channel should be automatically chosen by the router. That said, I limited the available channels on the 2.4 GHz band to just 1, 6 and 11. The HW2 is only one frequency band at a time, so I don't know what to expect for the 5 GHz frequency band.
The GuestsIoTisolated SSID is turned off at 3AM every day and then back on at 3:30AM. This was done just to provide a sample of scheduling things. Wi-Fi itself can be schedule (not just one SSID) as can firewall rules.
DNS and CONTENT BLOCKING
There are some Local DNS records that block a few ad/tracking domains such as ads.mopub.com, ads.nexage.com, ads.roku.com and ads.yieldmo.com. The blocking is done by forcing the domains to resolve to IP address zero. Here too, this is mostly as a demonstration of how the feature works. One innocent domain, atlanta.craigslist.org is also blocked, to provide a sample of what happens when a domain is blocked by DNS. Nothing against the city of Atlanta or CraigsList.
A similar feature, Content Blocking is also used to block some ad/tracker domains. Whereas DNS blocking is specific, Content Blocking is generic. For example, demdex.net is blocked with Content Blocking. This blocks anything that ends with demdex.net. It would, for example, block: abc.demdex.net, a.b.c.d.e.demdex.net and any.thing.demdex.net. Another difference is that DNS blocks all access to the target domain/subdomain. Content blocking only blocks website HTTP/HTTPS access. if abc.demdex.net was an email server, access to it would be allowed.
The most extreme example of generic blocking is when we block "cn" and "ru". This blocks every website in China and Russia. The sample also blocks websites ending in "cm" and "xyz" because they are frequently used by bad guys.
OUTBOUND FIREWALL RULES
Along with VLANs, support for outbound firewall rules is one of the best things about the Surf SOHO. There are 7 active and one inactive firewall rules, as you can see below.
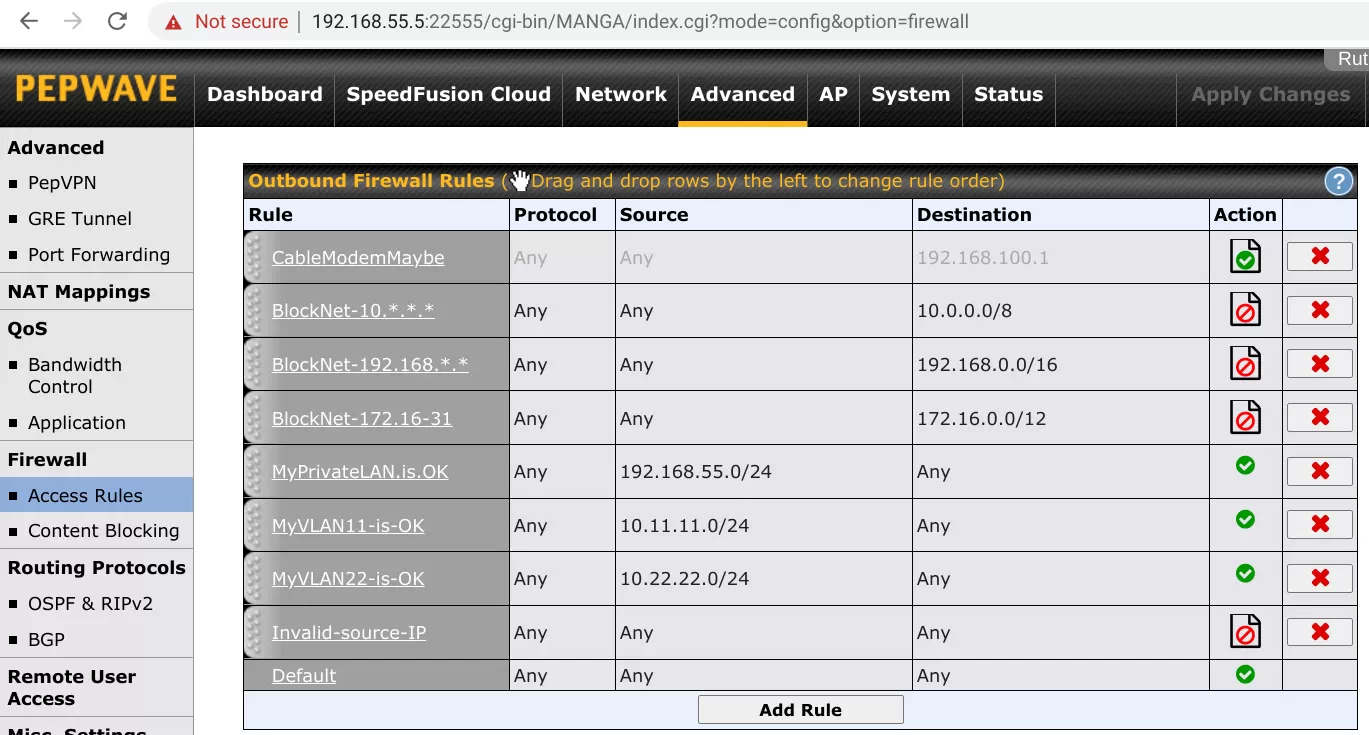
The rule CableModemMaybe is assigned to IP address 192.168.100.1 which is used by a number of cable modems. If you have a modem that is addressable by IP address you can use a firewall rule to either block access to it from the LAN or, at the least, audit all access to the modem.
The next three firewall rules (they all start with Block) block access to three groups of internal-use-only IP addresses. No packet of data should ever leave the router destined for one of these IP addresses. Yet, I see it all the time. Blocking these IP addresses has not been a problem for me and I have done it for years. Sometimes this happens so often, that I disable the logging.
The next three rules (they all start with My) are focused on the source IP address rather than the target. This configuration uses three subnets (192.168.55.x and 10.11.11.x and 10.22.22.x) and any data leaving the router from one of these subnets is allowed. The final rule (Invalid-source-IP) blocks and logs whatever is left. Nothing should be left. Yet . . .
FINALLY
Some minor things:
- You will want to change the time zone (System tab -> Time). It is set to US Central time
- InControl is disabled (System -> InControl)
- The DSL/Cable optimization option is turned on (Advanced -> Application). If you have an optical Internet connection (such as FIOS) then turn this off. I enabled this because optical connections are usually much faster than the maximum speed of the Surf SOHO.