Our Standard Operating Procedure isn't hard: we see an available Wi-Fi network, click on it and enter the password. Yet, back in 2007 this was deemed too hard, so WPS was introduced to make Wi-Fi access easier.
The WPS protocol in consumer routers is like putting a virtual HACK ME sign on the box. WPS was a bad idea to being with, has a huge design flaw, comes from an unstrustworthy source and is overly complicated. In addition, there have been multiple instances of poorly written, buggy implementations.
It is better to use a router that does not support WPS at all. If your does, try to turn it off, then verify that it really is off using the software mentioned near the end of this page.
A typical consumer router supports WPS, a typical business class router does not. My favorite router, the Pepwave Surf SOHO, does not support it. A March 2017 article in PC Magazine, The Best Wi-Fi Mesh Network Systems of 2017 describes nine different mesh router systems. Six of the nine do not support WPS, which I take as progress considering that the devices are targeted at consumers. The three that do support WPS are the Netgear Orbi, Amped Wireless Ally and Luma.
You have to wonder if the design of WPS stems from incompetence or if it was intended for spying. Arguing on the side on incompetence, is that WPS comes from the WiFi Alliance, the same group that gave us WEP encryption.
WPS Is a Bad Idea
A visitor to your home/office illustrates one aspect of why WPS is a bad idea The visitor only needs to turn your router upside down, take a cellphone picture of the label on the bottom and they can, thereafter, get into your WiFi network. The WPS password (they use a different term, but its a password) on the router label is the equivalent of a get out of jail card in Monopoly. It over-rides the WPA2 password.
Have a really long WPA2 password? It doesn't matter, WPS lets the visitor in anyway. Change the WPA2 password every week? It still doesn't matter, WPS continues to let the one-time visitor into your network.
But, a visitor with a cellphone is only part of the security problem with WPS.
WPS Is Complicated
There are multiple modes of operation in WPS. Only one has an obvious security flaw but routers, as a rule, do not support enabling/disabling the various modes of operation. I am no expert on the assorted operational modes. That said, one mode is geared to setting up and configuring a new WiFi network on a new router. This is mode that gave the protocol its name: WiFi Protected Setup and it is not the operating mode with the security problem.
Three other operating modes allow a new WiFi client to logon to an existing WiFi network. They are illustrated in the screen shot below from a Linksys EA6200 router running firmware 1.1.41.164830. (FYI: see how an Altice router handles WPS configuration here.
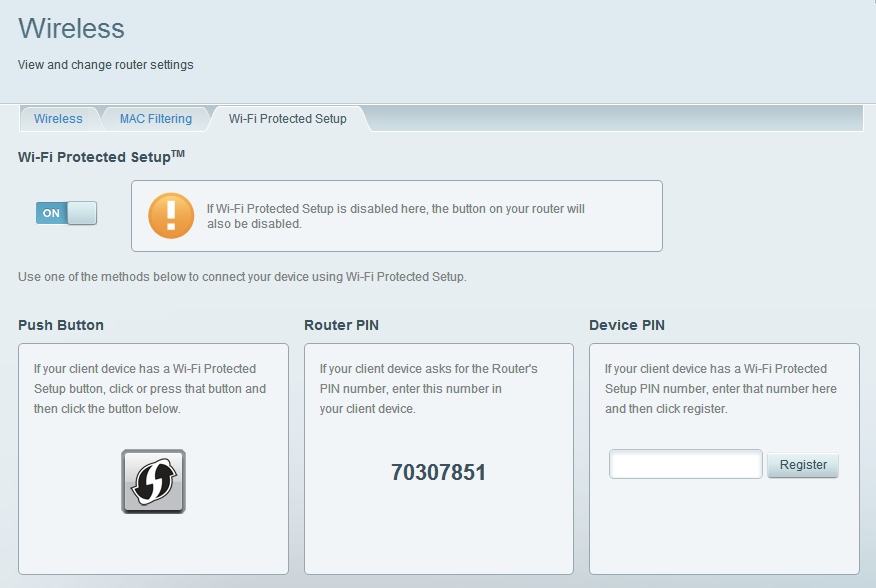
One of the logon modes (shown on the left in the picture above) requires pushing buttons on both the router and the WiFi client. In this case the button is virtual but many WPS capable routers have a physical button, which the warning above references. Like a Bluetooth pairing, this type of WPS pairing is only active for a minute or so before it times out. Instructions from Netgear on using push button mode (How do I use Wi-Fi Protected Setup (WPS) to connect to my WiFi network?) say that the pairing is active for two minutes. I believe the official term for this mode of operation is Push Button Connect or PBC for short.
The appeal of push-button WPS is that it's so easy. Below are the instructions for connecting a Wi-Fi enabled Brother printer to a WPS-enabled network. Push one button, push another and you're done. This is the only place I have seen to use the term AOSS as a synonym for WPS.
I suspect the Netgear Arlo Pro security camera uses the push button mode of WPS. The camera talks to a Netgear base station on a Wi-Fi network created by the base station. That Wi-Fi network supports WPS. The camera is linked to the base station by pushing buttons on the devices.
Push button mode does not have any remote security problems. Locally however, anyone that can touch a router with a physical WPS button, can get onto the Wi-Fi network. And, changing the password will not block this WPS-provided access.
In between local and remote is the kid next door looking for a network to break into. If desperate enough, they might setup a Wi-Fi device to send a WPS pushbutton connection request every 20 or 30 seconds. Sure, this will fail for months on end, but it only takes one success.
Apple supports a mode of WPS they call "First attempt" for connecting WPS printers to the network. This uses the push-button method. It's not clear to me how Apple limits the functionality to just printers. I read the Setup Guide for an Apple router and the topic was not explained.
The mode of operation on the far right, which Linksys calls Device PIN, involves entering a serial number (a.k.a. PIN) associated with a WiFi device into the router. This mode too, does not have security problems as you first have to login to the router to use it. I have also seen this referred to as Client PIN mode. Apple AirPort routers use this to connect a WPS printer to the network.
There is also another mode of WPS operation, not shown above. It is the latest mode: NFC or Near Field Communication. If both the router and the wireless device support NFC then you can get on a wireless network just by touching the device to the router. If the router is offering multiple networks, such as a private 2.4GHz, a private 5GHz and a Guest, I have no idea which network the NFC device is assigned to.
I think there used to be yet another mode, that used a USB flash drive to transfer network configuration information.
The problematic mode, Router PIN, is in the middle box in the screen shot above. In this mode, when a new WiFi device wants to get on the network it can do so by providing the router with the hard coded WPS password (the technical term is "pin code") of the router. That set-in-stone WPS pin code is whats on the label on the bottom of every WPS capable router. In the screen shot above, we can see that the WPS PIN code for this router is 70307851.
Cisco, in their documentation for their RV215W router, Basic Wireless Settings Configuration on RV215W refers to the three modes of operation as WPS Method 1, 2 and 3. Despite this having been last updated in November 2018, it still says that WPS is secure. Not true.
Design Flaw
The obvious problem with the Router PIN code mode of operation is that WiFi clients can guess, and guess and guess again, until they hit on the right code. At first it seems that 8 digits (the PIN codes are all numeric) should be enough to avoid mass guessing, but there is a HUGE design flaw that converts 100 million to 11 thousand.
An 8 digit number should mean that there are 100 million (zero through 99,999,999) possible codes. But no.
The last digit is a checksum, so we are down to 7.
The 7 digits however are not validated a single number. Instead, the WiFi device first offers the router 4 digits, gets that validated, then offers the last 3 digits for validation. Four digits is 10,000 possibilities. Three digits is 1,000. Adding them up yields the 11,000 mentioned above.
Anyone guessing would, on average, only need to make half the possible guesses before hitting pay-dirt. That gets us down to 5,500 guesses. It doesn't take computers very long to make 5,500 guesses.
Bottom line: anyone near a router that supports WPS can hack into it in a matter of hours. We may never know if the protocol was purposely designed this way to allow spying.
And, WPS is not just in routers. I have seen an Android v4.4 cellphone that had WPS turned on when it was used as a "Mobile Hotspot", sharing its 4G/LTE data connection via Wi-Fi. There was no way to disable this either. I have not tested Android 5, 6 or 7. Or, an iPhone either.
Software to make the 11,000 guesses is freely available in Kali Linux. It's called Reaver.
WPS Programming Bugs
On top of this insecure design, we have also seen coding issues. While the WPS spec calls for routers to limit massive guessing of the PIN code, not all routers do so. In addition, back in December 2011 when the you-know-what first hit the fan about WPS, there were some routers that did not disable WPS, even after being told to do so.
More bugs have come to light in the years since. There have been at least four cases of bad coding that reduced the number of necessary guesses to well below 11,000. For details, see the reading list at the bottom of this page or the router bugs page. An April 2015 article by Paul Ducklin, We TOLD you not to use WPS on your Wi-Fi router! We TOLD you not to knit your own crypto! offers a good introduction to three different WPS programming flaws.
Detecting WPS
Want to check if your WiFi network supports WPS? As a rule, operating systems won't tell you. That is, the feature that scans for nearby networks and displays them, does not say anything about WPS. This is true for OS X, iOS, Windows, Android and Chrome OS. Apple, I believe, does not want iOS users to know. I know of no iOS apps that display the WPS status of a Wi-Fi network.
On Windows, the free and portable WifiInfoView by Nir Sofer displays a ton of technical information about detected Wi-Fi networks, including whether they support WPS or not. When WPS is enabled, the status is either Configured, Not Configured, or Locked. A value of "No" means WPS is not enabled. This screen shot shows about half the available information from WifiInfoView. I blogged about the program in Sept. 2017: WifiInfoView is a great Wi-Fi utility for Windows. Mr. Sofer is an excellent source for Windows software.
On macOS, the Standard edition of WiFi Explorer by Adrian Granados-Murillo displays the WPS status of Wi-Fi networks. The Standard Edition costs $20. WPS information is also available in the more expensive Pro edition but is not shown in the free Lite edition. When WPS is enabled, WiFi Explorer shows the same status values as WifiInfoView: Configured, Not Configured, or Locked.
On Android, the Wi-Fi Analyzer app by farproc shows if WPS is supported for each detected SSID. Unlike the previous two programs, this one only displays an On/Off status. If WPS is disabled, it shows nothing, when it is enabled, it displays "WPS". In this screen shot from the app, three of the detected Wi-Fi networks are using WPS.
Another Android app, also called WiFi Analyzer, also displays the WPS status. This one is open source and from VREM Software.
If you know of other software that reports on WPS, please let me know.
These programs beg the question, what do the three status values (Configured, Not Configured and Locked) really mean? Searching for the answer turned up little, but Adrian Granados-Murillo, the developer of WiFi Explorer, was kind enough to provide these definitions:
Configured: The SSID, security and other settings of the access point (or router) have been successfully configured.
Not Configured: The access point (or router) settings need to be configured
Locked = The access point (or router) has locked its PIN, either due to too many authentication failures or a brute force attack
If none of these three states are shown in Wifi Explorer, then WPS is either disabled or not supported.
No doubt, the Configured/Not Configured statuses relate to a now-forgotten purpose of WPS, the setup a new router; one of many bad ideas from the Wi-Fi Alliance. WPS, after all, stands for Wireless Protected SETUP. These statuses must indicate if the initial setup has been done or not.
I ran a test with WifiInfoView in an area with many Wi-Fi networks and found
87 SSIDs had a status of CONFIGURED
35 had a status of NO
5 had a status of LOCKED
So, it appears that "Configured" means WPS is enabled and "Not Configured" is a relic of the past. Interestingly, all of the "Locked" networks were from HP OfficeJet printers.
Note what we can not tell. There is no status that tells you if push-button mode is enabled or not. There is no status that tells you if log-in-to-the-router-and-enter-the-WPS-key-of-a-WiFi-device mode is enabled. And, of course, nothing tells you if the most dangerous mode, guessing the WPS key of the router, is enabled.
As for the HP OfficeJet printers with a locked status, this was, at first, a mystery. This HP page, Connecting your wireless printer talks about the HP printer as a Wi-Fi client connecting to an existing router using the WPS push button mode. There is also an HP Auto Wireless Connect option, but again, the HP printer is a Wi-Fi client, it is not creating a Wi-Fi network.
But, the SSIDs of the printers, shown below, gave the secret away. In the list below XX represents two hexadecimal characters.
DIRECT-XX-HP OfficeJet 4650
DIRECT-XX-HP OfficeJet 3830
DIRECT-XX-HP OfficeJet Pro 6970
DIRECT-XX-HP OfficeJet Pro 6960
Clearly these SSIDs are for Wi-Fi Direct, a version of Wi-Fi that lets two devices communicate directly without a router in the middle. To allow phones and tablets to print to an HP printer, the printer creates these SSIDs for the phones and tablets. The phones and tablets need not know anything about Wi-Fi Direct. Wi-Fi Direct uses WPS to make the connection using either Near Field Communication, a PIN, Bluetooth or a button press. This article points out that Wi-Fi Direct is different from ad hoc Wi-Fi networks.
Mesh Routers that do not support WPS
Frequently asked security questions by Eero. Quoting: "eero doesn't support WEP, WPA, or WPS, as these protocols are known to be insecure."
Google Wifi security features Quoting: "WPS, a mechanism that lets a device join a wireless network without entering a password, is also not supported for security reasons."
Does Plume support WPS? Quoting: "Plume does not not support WPS as it was discovered to be a less secure procedure for establishing a WiFi network."
System specs published here Tenda MW6 Nova Whole Home Mesh WiFi System Reviewed (by Tim Higgins Feb 8, 2018) show that it is not supported.
An Oct. 2016 Luma blog posting by Yasin Jabbar said "Our Luma WiFi routers natively don't support WPS." Luma is no longer in business, at least not using that name, the company was acquired.
New Mesh Routers that support WPS
The Synology MR2200ac supports WPS according to this May 2019 review.
The D-Link Covr supports both WPS pin code mode and push button mode. A screen shot of the admin interface shows that each mode can be enabled or disabled separately. (Added September 4, 2017)
Oct 9, 2017: Initially the Ubiquiti AmpliFi routers and mesh points did not support WPS. This factored into my decision to buy two systems for people I know. Then, WPS was half added in firmware 2.2.2. I say half because I detected it with Wi-Fi scanning software but the company said nothing about it anywhere. The mobile app ignored it so you couldn't disable it. This is shameful; add an insecure feature, say nothing about it and don't let customers disable it. As of firmware is 2.4.2 the app does include WPS and it is off by default. The firmware release notes say nothing useful and the User Guide still says nothing at all. The app says that if you press the display on the router, WPS is enabled for two minutes. I asked tech support about this and they said that AmpliFi only supports push button WPS, which is not a huge security issue. I have no confirmation of this however. And, even the push button method lets anyone who can touch your router get online. Not good security.
Dec. 13, 2017: After remotely controlling an AmpliFi for a few months, I was physically next to it recently and ran a scan of nearby networks with the Android Wi-Fi Analyzer app. It shows that the AmpliFi network was WPS enabled even though this feature was turned off in the Android app. And, I checked the User Guide for WPS and there is not one mention of it at all. The online FAQ has just a one sentence mention of it when the feature was introduced. The total lack of documentation is the sort of laziness that will prevent me from recommending AmpliFi in the future. No reason for this.
Dec. 14, 2017: Four strikes against WPS.
- Tech support said "The reason the WiFi analyzer still shows as WPS enabled even though its disabled in the app, is because the mesh points have inbuilt WPS enabled by default ... " This not true. While the mesh points may have inbuilt WPS (not sure how I could verify this), the AmpliFi network in question had no mesh points, only two routers.
- Even if the mesh points were the reason, it means that WPS can not be completely disabled, which is bad, very bad.
- I was told seemingly conflicting things regarding WPS. In October 2017, tech support said that only the push button type of WPS is supported. If that were true, then I can't see how the mesh points would be involved as the only button you can push is on the router.
- There is no documentation about WPS and AmpliFi. Not a thing.
Does my Orbi WiFi System support Wi-Fi Protected Setup (WPS)? from Netgear. Article ID: 31239 Last Updated:03/29/2017. Quoting: "Yes. You can use the Sync button on your Orbi router and satellite to connect devices that support WPS." More details are available in the Orbi WiFi System User Manual (PDF) from March 2017. Reading page 23 (WiFi Connection Using WPS) makes it seem that Orbi only supports the push button method of WPS. While this is much more secure than the PIN method, it does still mean that anyone that can physically touch an Orbi can get on its network. The manual says nothing about whether this WPS feature can be disabled, so we have to assume it can not.
Linksys Velop User Guide (PDF). The manual has no date or release level which is always a bad sign. Page 17 describes how to "Connect a Device with WPS" and says "Wi-Fi Protected Setup allows you to easily connect wireless devices to your Wi-Fi without manually entering security settings." The screen shot of the mobile app shows it saying "WPS is a secure way for basic users to connect devices without complicated authentication details." Sane people disagree about WPS being secure. And, what the heck is a basic user? From the screen shot, it looks as if WPS can be disabled but the manual does not go into this at all. Perhaps most importantly, it is not at all clear which types of WPS are supported. At least Netgear was clear on this point.
The Asus Lyra mesh system seems to support WPS. Whether it does or not is none of our business. You can't look it up in the User Guide as there is no User Guide to download from the Asus website. I infer WPS support based on two things. For one, this picture of the underside of a Lyra shows a PIN code. Then too, they have a pairing button that can be used to add the second and third Lyra thingies to the network after the initial one is up and running. This sounds like the WPS pushbutton method.
Routers that can not disable WPS
The Netgear Nighthawk X4 R7500 v2 can not disable WPS. I tested this in January 2019 using the latest firmware at the time, version 1.0.3.40.
The D-Link DIR 890L as per this article.
The Ubiquiti AmpliFi mesh router system (see above for more).
Client Operating Systems and WPS
As I always disable WPS, my experience using it is not extensive. But in January 2019, I started evaluating the security of assorted routers and thus experimenting. One thing to note: after using WPS to get on a network once, WPS does not need to be used again. WPS hands over the Wi-Fi password to the router client device (comptuer/tablet/phone,etc) where it is saved, just like a normal password based logon.
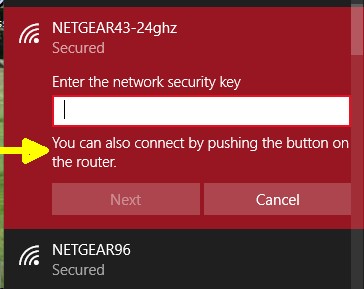
Windows 8, like all OSs, presents a list of detected nearby wireless networks. When you click on a network supporting WPS, it both asks for the password and tells you that, instead of the password, you can click the WPS button on the router. If you click the router WPS button, you should be logged on to the network in a few seconds. Windows 10 (shown at right) works the same, saying "You can also connect by pushing the button on the router". According to this article Windows 10 does not generate a WPS client PIN code.
Android 9 does not support WPS. Android 7 and 8 both do support it. Interestingly, WPS on Android 7 and 8 is not an option when you click on a nearby network to connect to it. WPS on Android is more a Wi-Fi thing than a specific SSID thing. With Android devices the button is virtual, you "push" it by touching the screen.
On Android 8, turn on Wi-Fi, from the list of nearby networks, go to WLAN Preferences, then Advanced. The virtual WPS button is the text "WPS Push Button". On Android 7, turn on Wi-Fi, from the list of nearby networks, go to Advanced Wi-Fi options, to find the virtual "WPS Push Button". Either the virtual Android button or the real router WPS button can be pushed first, but they both have to be pushed within 2 minutes of each other.
Android 7 and 8 also support the WPS client Pin method, where the Android device generates a temporary 8-digit number that you manually enter into the web interface of the router. The same section of the Wi-Fi settings that has the virtual "WPS Push Button" also has the "WPS Pin Entry" which generates the number.
iOS does not support WPS, at least when version 12 was current. I don't know if older versions supported it.
ChromeOS does not support WPS. I verified this by testing Version 71 in February 2019.
Further Reading
My blog from April 28, 2017: How seven mesh routers deal with WPS.
March 2018: YouTube video by Null Byte Hack WPA & WPA2 Wi-Fi Passwords with a Pixie-Dust Attack using Airgeddon. Quoting: "... many routers have a flaw in the WPS setup pin feature that makes bypassing any WPA-based security trivial. Using a tool called Bully, we can exploit weak entropy in the keys many routers use to encrypt the WPS pin, allowing us to break the WPS setup pin in vulnerable routers to dump the Wi-Fi password. We will use the WPS Pixie-Dust attack option in the Airgeddon wireless attack framework..." The Pixie Dust attack is possible on routers that do a miserable job with randomness. A router vulnerable to a Pixie Dust attack can be hacked without brute force guessing of the WPS pin code.
In November 2018, the German government created security guidelines for router manufactures. Their take on WPS was: "The router may implement Wi-Fi Simple Configuration (WSC) ... to provide an easier way of registering user devices at the router. Push Button Configuration (PBC) and USB Flash Drive (UFD) MAY be offered. Personal Identification Number (PIN) based WPS may only be used, IF the feature is deactivated in the initialized state and a new PIN is generated for each newly registered device."
Talk Talk is a British ISP and telco. In May 2018, their routers were confirmed vulnerable to the classic WPS pin code attack. You can't make this stuff up. The flaw was discovered by a company called IndigoFuzz using a Windows program called Dumpper. You have to be within Wi-Fi range to attack a vulnerable router. For more see the Bugs page under May 2018.
Trustwave SpiderLabs Security Advisory TWSL2018-004 A bug affected 6 Netgear routers. When the WPS button is pressed, the router allows WPS-capable clients to connect during 2 minute period without providing any credentials (expected behavior for WPS). However due to a bug, WPS clients can execute arbitrary code on the router as root during the same setup phase. In other words, if an attacker can press the WPS button on the router, the router can be completely compromised. This was found by Trustwave in March 2017 and Netgear released a patch in October 2017. An advisory was published in February 2018.
How do NETGEAR Home routers defend WiFi Protected Setup PIN against brute force vulnerability? Article ID: 19824 Last Updated: Nov. 28, 2016. After too many wrong PIN code guesses, Netgear routers stop taking new guesses for a while. Also, you can disable WPS PIN code mode but still use push button mode.
How to stop Wi-Fi hackers cold by Roger A. Grimes in InfoWorld May 26, 2015. The author helps out a neighbor whose router was being used by a bad guy to download illegal material thanks to WPS. Quoting: "Nearly every new feature intended to make computer security easier is bound to open up new vulnerabilities. Such is the case with WPS."
This April 2015 review of the $300 D-Link DIR 890L/R router at SmallNetBuilder.com points out that it does not let you disable WPS.
Evading WPS Lockouts on Routers? by RedPanda at NullByte April 7, 2015. Some routers implement rate limiting as a defense against brute force pin code guessing.
We TOLD you not to use WPS on your Wi-Fi router! We TOLD you not to knit your own crypto! by Paul Ducklin for Sophos April 2015. This describes two different bugs in programming WPS. Fairly technical. Sophos offers router software, the Sophos UTM that does not support WPS.
Reversing Belkin's WPS Pin Algorithm By Craig April 10, 2015. Exposing bad WPS programming by Belkin.
Reversing D-Link's WPS Pin Algorithm by Craig October 31, 2014. Exposing bad WPS programming by D-Link.
Using WPS on your Wi-Fi router may be even more dangerous than you think by Paul Ducklin for Sophos September 2, 2014 Describes the research by Dominique Bongard in the article below. The programming flaw he discovered converts a normally on-line WPS attack to off-line. Bad guys no longer need to make 11,000 guesses to the router. Off-line guessing attacks the WPS protocol itself and can yield the WPS pin code. There are bugs in at least two unspecified routers.
Offline bruteforce attack on WiFi Protected Setup by Dominique Bongard. Aug 6, 2014
Wi-FI Protected Setup (WPS) is Insecure: Here’s Why You Should Disable It by Chris Hoffman November 24th, 2013. Has an overview of the PIN and push-button connection methods. Ignores the other types of WPS.
Routers using WPS are intrinsically unsafe by Fred Langa in Windows Secrets newsletter Dec. 13, 2012. This explains four WPS methods of gaining network access, explains the security problem, offers advice on router configuration and verifying that WPS is really disabled. Not a great article, has some mistakes and omits the fact that Android network scanners can display the WPS status.
Putting Wi-Fi router's security to the test by Fred Langa Dec. 20, 2012. This is a follow-up article to the above that walks you through creating a BackTrack 5 Linux DVD, installing Reaver on it and setting it loose on a WPS enabled Wi-Fi router. A great way verify that WPS is really disabled and, as far as I know, the only way to tell if a router will stall or lock out an attacker after too many bad PIN guesses.
Waiting For The WPS Fix by Tim Higgins Jan. 7, 2012. Vendor responses right after the initial news.
Hands-on: hacking WiFi Protected Setup with Reaver by Sean Gallagher of Ars Technica Jan. 4, 2012. Ars being ars. Even with WPS supposedly disabled on a Linksys WRT54G2 Wireless-G Broadband Router, Gallagher was able to get it to cough up the SSID and password.
Wi-fi Protected Setup (WPS) Vulnerability Exploited by Tom at thesysadmins.co.uk Jan. 4, 2014
Researchers publish open-source tool for hacking WiFi Protected Setup by Sean Gallagher of Ars Technica Dec. 30, 2011. Quoting: "The routers most vulnerable to these attacks ... include products from Cisco's Linksys division, Belkin, Buffalo, Netgear, TP-Link, ZyXEL, and Technicolor. None of the vendors has issued a statement on the vulnerability, or replied to inquiries from Veihbock."
Brute forcing Wi-Fi Protected Setup When poor design meets poor implementation by Stefan Viehbock December 26, 2011. The original research that exposed the design flaw in WPS.
CERT Vulnerability Note VU#723755 WiFi Protected Setup (WPS) PIN brute force vulnerability. Dec 27, 2011. Big publicity at the start.
New Tools Bypass Wireless Router Security by Brian Krebs December 29, 2011. More publicity at the start.
Most Wi-Fi routers susceptible to hacking through security feature by Chester Wisniewski for Sophos December 30, 2011.
The Woops of WPS (Wi-Fi Protected Setup) raises its ugly head again by me April 2014. Basically, I am griping that articles about the new NFC flavor of WPS completely ignore the security problems with it.
Wi-Fi routers: Oldies are goodies by me January 2012. When I first learned of the WPS security problem, my router at the time did not support it because it was so old, it pre-dated WPS.
Wi-Fi_Protected_Setup at WikiPedia
Wi-Fi Protected Setup (WPS): The Easiest Way to Set Up Wireless Devices by Sharan Keswani July 12, 2011. A D-Link blog touting the WPS push button.
Apple routers
Apple routers support WPS, but only partially.
For one thing, they seem to only support it for adding WPS enabled printers to the LAN. The AirPort Extreme Setup Gide says nothing about using WPS to connect anything other than a printer to the network. How the router can tell a printer from another type of wireless device is unclear to me. Since WPS is a standard published protocol, any type of device should be able to communicate using the protocol. In fact, someone said that in older versions of the AirPort utility, the feature was called 'Add Wireless Clients'.
In addition, Apple does not seem to support all the various WPS modes of operation. According to the AirPort Extreme setup guide, it supports a mode where you enter a number from the assumed printer into the router. This mode was never a security risk. It also supports another mode that Apple calls "First attempt" for, again, connecting a WPS printer to the network. The Setup Guide does not explain this mode at all. But, while Apple does not seem to update the Setup Guide, the do update their website. The document, Connect an AirPrint printer to a Wi-Fi network (last updated June 1, 2015) says "If you selected 'First attempt,' push the WPS button on the printer. When the printer's MAC Address appears in AirPort Utility, click Done." Outside of Apple, this is called the WPS push button method. It too, has never been a security issue.